

In this article, you will find a detailed analysis of one of the most sophisticated and dangerous malware today – LockBit, which uses the latest SwitchSymb technique to enhance its attacks. You’ll learn how this malware has evolved to bypass traditional cyber defense methods, posing a significant risk to organizations around the world.
We recently discovered a Business Email Compromise (BEC) campaign that has been going on since at least the third quarter of 2022. The campaign targets German-speaking companies in Germany, Austria and Switzerland. As with many other BEC campaigns, attackers register domains that differ by only one or two characters from the target organization’s domain. In this case, for an unknown reason, the address in the Reply-to header (the address to which the sender wants to receive a reply) differs from the sender’s address in the From header; the address in the Reply-to header does not use a domain that mimics the domain of the target organization.
Unlike targeted attacks that compromise corporate email, conventional phishing campaigns are very primitive and can be automated. An example of such automation is the SwitchSymb phishing kit. At the end of January of this year, there was a sharp increase in the number of emails sent as part of one of the phishing campaigns we monitor. This company targets corporate users. After analyzing the received phishing emails, we found a link to a form to confirm the email address.
When the recipient clicks on it, they are taken to a page with a domain that mimics the organization’s domain. The phishing website that this page links to is being used by multiple campaigns at the same time. This can easily be seen by changing the URL of the page, particularly the details of the user being attacked on it. In this case, only one instance of the phishing kit is running on the server.

LockBit is one of the most active extortionist groups that attacks companies all over the world. At different times, attackers have used malicious code from other groups, such as BlackMatter and DarkSide. This approach makes it easier for potential partners to manage encryptors.
In February of this year, we found a new variant, LockBit Green, based on code from the defunct Conti group. We compared the code of the two encryptors and found that LockBit Green contains 25% of Conti’s source code.

The code borrowed from Conti contains three pieces: a ransom demand, command-line options, and an encryption scheme. Using a ransom note makes no sense. There is no satisfactory explanation as to why the attackers did this: the Conti code options were added to the LockBit command line options and became available for use. In general, LockBit Green supports the following command line options:
After all, the attackers borrowed Conti’s encryption scheme. They use a custom implementation of the ChaCha8 algorithm, which encrypts files using a randomly generated key and a one-time code that uses a hard-coded RSA public key to store and encrypt.

We recently discovered that a ZIP file downloaded to a multiscanner contains LockBit samples for various architectures: Apple M1, ARM v6, ARM v7, FreeBSD, etc. Of course, we had our doubts about what their code looked like, and a simple analysis of the ZIP files revealed that all the samples belonged to the Linux/ESXi version of LockBit.
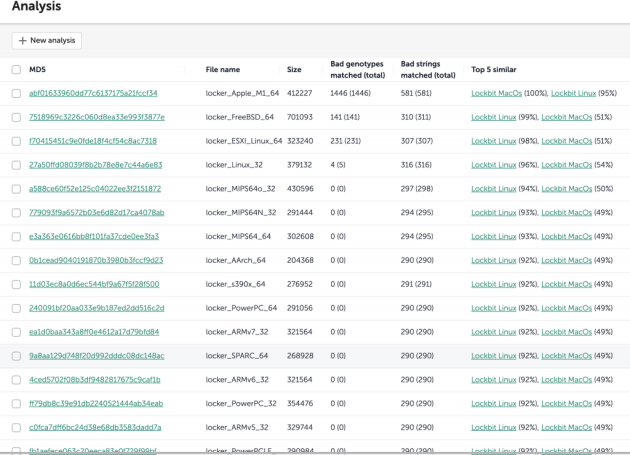
Our further analysis revealed that Rockbit has tested variants of the cipher for different architectures, but has not yet used them in real attacks. For example, the macOS samples are not encrypted and cannot be run on the target system. Additionally, string encryption uses a very simple XOR method with a single-byte key. However, the research findings suggest that LockBit will soon launch cross-platform attacks.

