Malware is a type of software designed to harm, use, or gain unauthorized control over a computer system. It can include viruses, trojans, worms, spyware, ransomware, and other types of malware. Malware can cause a variety of problems, including data theft, system crashes, and significant financial losses. To protect computer systems from potential threats, it is important to have a solid anti-malware strategy. Malware is a significant threat to computer systems that can lead to data theft, system crashes, and financial losses. It includes various malicious programs such as viruses, trojans, and ransomware. A strong anti-malware strategy, including software and employee training, is critical to preventing or mitigating malware attacks.Malicious software, or malicious software, is a type of program designed to harm computer systems, steal sensitive data, or gain unauthorized access. It can be distributed in a variety of ways, such as email attachments, downloads, or social engineering tactics.
Malware can take many forms, including viruses, worms, trojans, spyware, adware, and more. These malware can have a devastating impact on businesses and individuals, resulting in data loss, system downtime and financial losses. It’s important to have a reliable and up-to-date anti-malware solution and train employees on best practices to prevent malware attacks.
njRAT — is a RAT with powerful data-stealing capabilities. In addition to login keystrokes, it is capable of accessing the victim’s camera, stealing credentials stored in browsers, downloading and uploading files, executing processes and file manipulations, and viewing the victim’s desktop. RATs help an attacker gain remote access to a full GUI, control the victim’s computer without his or her knowledge, and are capable of performing camera screening and capture, code execution, keylogging, file access, password capture, registry manipulation, and more. It infects victims through phishing attacks and drives via downloads and spreads via infected USB keys or network drives. It can download and run additional malware, execute shell commands, read and write registry keys, take screenshots, log keystrokes, and spy on webcams. The njRAT Trojan can be used to control botnets (a network of computers) by allowing an attacker to update, remove, disconnect, restart, close the RAT, and rename its company ID. An attacker can additionally create and configure malware to distribute via USB drives using the Command and Control server software.
Create a server with njRAT. Remotely access the target machine.
Windows 10 (criminal). Windows 7, 8 or Server (Target).
Log into Windows 10 and install njRAT. Run njRAT, a GUI will appear and a pop-up window will appear asking you to specify the port you want to use to communicate with the target machine. Use the default port number 5552 and click Start.
Click “Designer” in the lower left corner.
In the Builder dialog box, enter the IP address of the attacker’s computer – Windows 10, check the Copy to StartUp and Registry StarUp options, and then click Build as shown below:
Save the file and name it as Example.exe. Now we need to use any technique to send this server to the desired destination by mail or any other means. To make this lab easier, I copied the Example.exe file to a network share.
In this lab, I am using a Windows 7 SP1 virtual machine.Note. Be sure to enable the firewall on the target machine. Drag the Example.exe file to the desktop and double-click it. As you can see below, the connection was successfully established.
Go back to Windows 10 (hacker). When the target double-clicks the server, the executable starts and the njRAT GUI running on Windows 10 establishes a persistent connection with the target machine as shown below: The GUI displays basic machine details such as IP address , OS.
Right-click on the detected target machine and select Manager. Double-click any directory in the left pane. You can right-click any selected directory and control it using context-sensitive options:
Click on Process Manager from the top menu. You will be redirected to the Process Manager, where you can right-click any process and perform actions such as Kill, Delete, and Restart.
Click Connections in the top menu and select a specific connection, right-click it and select Close Connection. This action breaks the connection between two machines that are communicating on a specific port.
Click “Registry” in the top menu and select the registry in the left panel, right-click the related registry files, several options will appear to manage them.
Click Remote Shell in the top menu. This action starts a remote command prompt on the target machine.
In the njRAT main window, right-click on the target machine and select “Run File”. An attacker uses these settings to remotely execute scripts or files from their computer.
Right-click on the target machine and select Remote Desktop Connection. This initiates a remote desktop connection without the consent of the target computer. You will be able to remotely interact with the victim machine using a mouse or keyboard. In the same way, you can choose the remote camera and microphone to follow the target and monitor the voice conversations.
Switch to Windows 7 (target machine). Suppose you are a legitimate user and perform some actions like login to any website or typing in some documents. Now go back to Windows 10 machine and right click on the target machine, select Keylogger option. A keyboard spy window will appear showing all keystrokes made by the target.
If the victim to disconnect by rebooting the machine, however, as soon as the victim logs in again, the njRAT client will automatically establish a connection with the victim.
HTTP/HTTPS trojans can bypass any firewall and work as a direct HTTP tunnel, but works the other way around. They use web interfaces and port 80 to gain access. Execution of these Trojans takes place on the internal host and spawns “child programs” at predetermined times. The child program appears to be a firewall user, so it allows the program to access the Internet. However, this child executes a local shell, connects to a web server owned by the attacker on the Internet via a legitimate HTTP request, and sends it a ready signal. A legitimate response from the attacker’s web server is actually a series of commands that the child can execute in the machine’s local shell. Network auditing for HTTP RATs is generally more difficult and important because most firewalls and other perimeter protection devices cannot detect the traffic generated by the HTTP RAT Trojan. Remote Access Trojans (RATs) are malicious programs that run stealthily on a host computer and give attackers remote access and control. A RAT can provide a backdoor for administrative control over a target computer. Once the target system is compromised, an attacker can use it to spread the RAT to other vulnerable computers and create a botnet.
Create a server and run an HTTP Trojan on Windows Server 2012. Run a server from a Windows 10 virtual machine.
Windows Server 2012 virtual machine (the attacker). Windows 10 Virtual Machine (Target).
Log into Windows Server 2012 and install the HTTP RAT TROJAN tool: (https://anonfile.com/HaT8v9Jbn7/HTTP_RAT_TROJAN_zip). Double click httprat.exe, HTTP RAT main window will appear as below:
Uncheck “Send notifications with IP address to mail”, enter server port 84 and click “Create”.
Once the httpsserver.exe file is created, a pop-up window will appear, click OK and allow the Windows 10 virtual machine to access the file. The file will be saved in the HTTP RAT TROJAN folder as shown below:
Now login to Windows 10 and navigate to the location where you saved the httpsserver.exe file. Double-click to launch the Trojan.
You will be able to see the Httpserver process in Task Manager:
Switch back to Windows Server 2012 and start a web browser. Enter the IP address of Windows 10 in the address bar to access the machine.
If everything works, you should get a window like this:
Click the Running Process link to view a list of processes running in Windows 10. You can kill any process from here.
Click Browse and then click Drive C to view the contents of that drive.
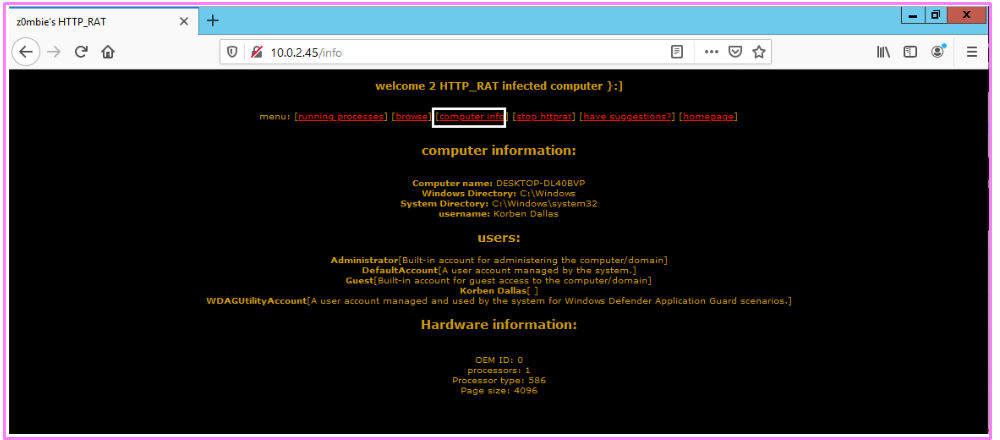
Click Computer Information to view information about the computer, users, and hardware.
SwazCryptor — an encryptor (or “encrypter”) that allows users to encrypt the source code of their application. Crypter is a software used to hide viruses, keyloggers or any RAT tools from antiviruses so that antivirus programs do not detect and remove them. It simply adds hidden values to each individual code in the source code. Thus, the source becomes hidden, making it difficult for AV tools to scan it.
How to encrypt a Trojan and make it partially/completely invisible.
Windows 10 virtual machine (attacker). Windows 7 or 8 virtual machine (Target).
Sign in to Windows 10. Launch a web browser and enter the URL: (https://antiscan.me). download the malware file created in the previous lab and run the scanner.
Download SwayzCryptor and run the program.
You can easily test if everything works with njRAT, share the malicious file with any Windows VM, run the file with njRAT opened on a Windows 10 machine.
REMnux — is a Linux-based toolkit designed for reverse engineering and malware analysis. It contains a set of free and open source tools that can be used for malware inspection and incident response. REMnux is designed to be used in a virtual machine, which helps protect the host system during analysis. It is used by malware analysts, incident responders and other security professionals.
Tsurugi Linux — is a new heavily customized Linux distribution (first release on November 3, 2018 at the AvTokyo security conference in Japan) based on Ubuntu 16LTS (64-bit with new custom kernel 5.4.2) and designed to support DFIR investigations, malware analysis and OSINT activities.
FLARE VM — is a free, open-source, Windows-based virtual machine designed for reverse engineering, malware analysis, and threat detection. It comes pre-configured with various tools such as debuggers, disassemblers and decompilers to analyze Windows malware and suspicious files. FLARE VM is maintained by the FireEye Labs Advanced Reverse Engineering (FLARE) team and is regularly updated with the latest analysis tools and plugins.
ProRat — is a remote administration tool written in C and capable of working with all Windows operating systems. ProRat was designed to allow users to control their own computers remotely from other computers. However, attackers used it for their own nefarious purposes. Some hackers take control of remote computer systems to launch a denial-of-service (DoS) attack that renders the target system unavailable for normal personal or business use.
Theef — is a Windows based client and server application. The Theef server is the virus that you install on the target computer, and the Theef client is what you then use to control the virus. Theef is a remote access trojan written in Delphi that allows attackers to remotely access the system via port 9871.
JPS Virus Maker — is a computer program that allows users to create their own computer viruses. It is usually used for educational or testing purposes to help users understand the behavior of viruses and how to protect against them. However, the program can also be used for malicious purposes, so you should be careful when using it. Creating and spreading viruses is illegal and can lead to serious consequences.
Regshot — is a great utility that you can use to compare the number of registry entries that have been changed during installation or system configuration changes. This is a great tool for troubleshooting and monitoring the registry. The purpose of this software is to compare your registry at two separate points by taking a snapshot of the registry before any system changes or when programs are added, removed, or changed, and then taking a second snapshot after the changes have been made and comparing them.