
Kali Linux is a popular Linux distribution widely used for software penetration testing and ethical hacking. It has an astronomical number of commands and tools for different purposes. The Kali Linux cheat sheet can be handy for quickly accessing these commands and finding the most useful ones. The Kali Linux Commands Cheat Sheet is an invaluable resource for cybersecurity professionals, ethical hackers, and IT professionals. It provides a comprehensive list of commands and tools for various cybersecurity tasks in the Kali Linux operating system.
This cheat sheet is available as a free PDF download and covers a wide range of functionality from intelligence gathering and vulnerability analysis to password attacks and access support. It is essential for quick reference and productivity during security assessment and penetration testing. In this article, you will find a comprehensive cheat list of commands for Kali Linux that is essential for cyber security and ethical hacking professionals. This resource helps users quickly find the commands they need to perform security audits, penetration testing, and other specialized tasks related to Kali Linux.
The Kali Linux Commands Cheat Sheet contains many types of commands for information gathering, vulnerability analysis,< /span> and more. Here is a list of frequently used kali Linux commands which can often be useful for kali Linux users.
Kali Linux has the largest collection of information gathering tools and commands. They are useful for gathering information about the target system and networks. Some of the more commonly used tools and commands of this type are listed below.
Vulnerability analysis tools and commands in Kali Linux help identify vulnerabilities in systems and networks, test the strength of passwords, and simulate attacks to identify potential weaknesses. Here is a list of popular tools and commands that are often used for vulnerability analysis
Various methods such as sniffing, spoofing, and cracking wireless protocols can be used for wireless attacks. Kali Linux has many commands and tools for applying these techniques. The following list contains the most useful of them.
Kali Linux comes pre-installed with many specially designed tools and commands for digital forensics. This allows forensic analysts to acquire, analyze and store digital evidence quite efficiently. Here is a short list of these types of tools and commands.
You can use the Kali Linux exploit tools to design and execute a wide variety of exploits, from simple command injection attacks to complex remote code execution exploits. The following list contains the most commonly used Kali Linux exploit tools.
Hardware hacking tools and commands are useful for identifying and exploiting vulnerabilities in various hardware devices. The list below contains a few of them.
Kali Linux has several powerful tools and commands available for reverse engineering tasks. You can use them to disassemble, decompile, and analyze binaries. Here is a short list of a few of them.
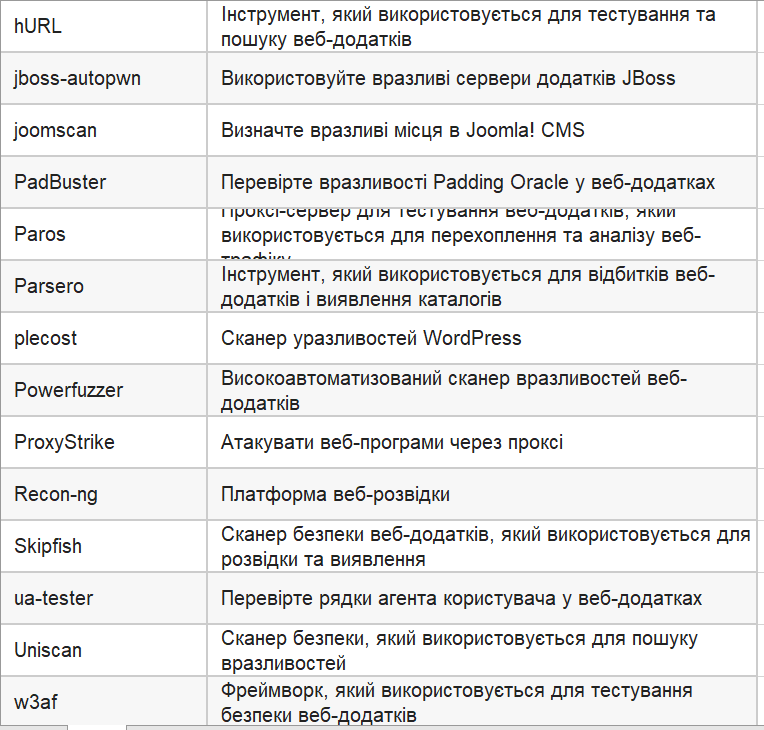
There are various tasks, including the discovery of network vulnerabilities, misconfigurations, and security issues in web applications. Kali Linux is well equipped to handle all of these. You can often use the following commands and tools to solve various problems related to web applications.

Stress testing is crucial and reflects the resilience of the system against any cyber attack. Several Kali Linux commands and tools related to stress testing are listed below.
Sniffing and spoofing are two common methods of intercepting and manipulating network traffic. Kali Linux provides a variety of commands and tools to intercept and detect spoofing. Check out some commonly used interception and spoofing commands and tools below.
It is important to create an accurate penetration testing report and share it with customers and stakeholders for a mutual understanding of system security risks. Kali Linux has tools like Dradis, MagicTree and more to manage, visualize and report penetration testing results.
Attackers use different types of passwords to gain unauthorized access to systems or networks. Using Kali Linux tools and commands, professionals can test security and password-related vulnerabilities.
A list of useful Kali Linux tools and commands to bypass security measures and maintain system access is below.
Kali Linux commands are useful for testing the security of systems and networks, and for detecting vulnerabilities by attackers. I believe that a compact list can be useful for professionals to remember the ideal commands and use the appropriate tools when needed. Please feel free to comment below if you find the list useful or have any suggestions for it.

