

Computers communicate using networks. These networks can be on a local LAN or connected to the Internet. Network sniffers are programs that collect low-level data on packets that are transmitted over a network. An attacker can analyze this information to discover valuable information such as user IDs and passwords. Wireshark is a powerful network analyzer that can be used to analyze traffic passing through a computer’s network interface. This may be necessary to identify and resolve network problems, debug your web applications, network applications, or sites. Wireshark allows you to fully view the content of a packet at all levels, so you can better understand how the network works at a low level. All packets are intercepted in real-time and provided in a human-readable format. The program supports a very powerful filtering system, color highlighting and other features that will help you find the packages you need. In this tutorial, we’ll look at how to use Wireshark to analyze traffic. The developers have recently moved on to work on the second branch of Wireshark 2.0, which has introduced many changes and improvements, especially to the interface.
We will use it in this article. Remember that Wireshark has display filters and capture filters. Here I look at the display filters that are entered in the main window of the program in the upper field immediately below the menu and icons of the main functions. To fully understand the meaning of the filters and what it shows, you need to understand how the network works. To familiarize yourself with the principles of network operation and protocols, it is recommended to study the cycle of computer networks.
Computers communicate by broadcasting messages on a network using IP addresses. Once a message has been sent across the network, the recipient’s computer with the corresponding IP address responds with its MAC address. Network analysis is the process of intercepting data packets sent over a network. This can be done using special software or hardware.
Collect sensitive data such as login credentials:
Listening to chat messages:
Capture files are transferred over the network.
Telnet
Rlogin
HTTP
SMTP
NNTP
POP
FTP
IMAP
The above protocols are vulnerable if the login credentials are sent in plain text:
Before we look at passive and active interception, let’s take a look at the two main devices used to connect computers to a network; hubs and switches.
A hub works by sending broadcast messages to all output ports on it except the one that sent the broadcast message. The recipient’s computer responds to the broadcast message if the IP address matches. This means that when the hub is in use, all computers on the network can see the broadcast message. It operates at the physical layer (layer 1) of the OSI model.

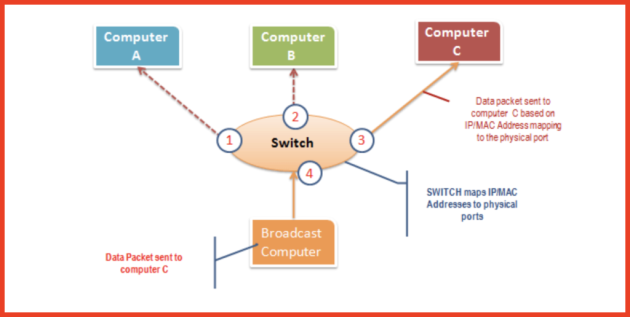
The switch works differently; it maps IP/MAC addresses to physical ports on it. Broadcast messages are sent to physical ports that match the recipient computer’s IP/MAC address configurations. This means that broadcast messages are seen only by the recipient’s computers. Switches operate at the link layer (layer 2) and network layer (layer 3).
Passive interception is the interception of packets transmitted through a network that uses a hub. It is called passive sniffing because it is difficult to detect. This is also easy to do because the hub sends broadcast messages to all the computers on the network.
Active interception is the interception of packets transmitted over a network that uses a switch. There are two main methods used to sniff connected network switches: ARP Poisoning and MAC Flooding.
In this hands-on scenario, we are going to use Wireshark to sniff data packets as they are transmitted over the HTTP protocol. For this example, we’ll analyze the network with Wireshark and then log into a web application that doesn’t use a secure connection. We will enter the web application at:
Login address – [email protected] , and password – Password2010 .
Note: We will log into the web application for demonstration purposes only. The technique can also sniff data packets from other computers that are on the same network as the one you are using to sniff. Sniffing is not only limited to techpanda.org, but also all HTTP and other protocol data packets.
The picture below shows the steps you should follow to complete this exercise without confusion.
Download Wireshark from this link http://www.wireshark.org/download.html
Open Wireshark:
You will get the following screen:
Select the network interface you want to sniff. Note that we are using a wireless network connection for this demonstration. If you are on a local network, you should select the LAN interface.
Click the “Start” button:
Open a web browser and type http://www.techpanda.org/
The login email is [email protected] and the password is Password2010
Click the send button:
A successful login should present you with the following dashboard:
Return to Wireshark and stop live recording:
Filter HTTP results using only the filter text field:
Immediately below the log entries there is a panel with a summary of the received data. Search for a summary specifying textual data based on rows:
application/x-www-form-urlencoded:
You should be able to view the text values of all POST variables sent to the server via HTTP.
MAC address flooding is a network analysis technique that fills a switch’s MAC address table with fake MAC addresses . This overloads the memory of the switch and forces it to act as a hub. When a switch has been compromised, it sends broadcast messages to all computers on the network. This allows you to sniff data packets as they are sent across the network.
Some switches have a port protection feature. This feature can be used to limit the number of MAC addresses on ports. It can also be used to maintain a secure MAC address table in addition to the one provided by the switch.
Authentication, authorization and accounting servers can be used to filter discovered MAC addresses.
Limiting network physical media greatly reduces the likelihood of a network sniffer being installed
Encrypting messages while in transit over a network greatly reduces their value because they are difficult to decipher.
Changing your network to a Secure Shell (SSH) network also makes it less likely that your network will be intercepted.

