

Hashcat was written sometime in mid-2009. Yes, there were already almost perfect working tools supporting rule-based attacks, such as “PasswordsPro”, “John The Ripper”. However, for an unknown reason, both of them did not support multi-threading. This was the only reason to write Hashcat: to take advantage of the multi-core nature of modern processors. True, it was not 100% correct. John the Ripper already supported MPI with a patch, but at the time it only worked for a Brute-Force attack. There was no solution available to crack MPI-enabled plain MD5 using rule-based attacks. Hashcat, since the first version v0.01, was called “atomcrack”.
This version was pretty bad, but at least the MD5 kernel was written in assembler using SSE2 instructions and was of course multi-threaded. It was a simple dictionary cracker, nothing more. But it was fast. Very fast. They were interested in this and after a week there were about 10 beta testers. Everything worked well, so requests for additional algorithm types, a rules engine for dictionary mutation, a Windows version, and different attack modes were added. These developments lasted about six months and were completely non-public. Then in version 0.29 “atomcrack” was renamed to “Dr. Hash.” Then with the release of version 0.30 to “hashcat”. The first official release of hashcat was v0.30, released on 12/24/2009. Starting with hashcat v0.40 released on 2012-08-05, Mac OSX binaries have been added. Hashcat is the world’s fastest and most advanced password recovery tool. The latest version combines the previous CPU-based hashcat (now called hashcat-legacy) and the GPU-based oclHashcat. Hashcat is released as open source software under the MIT license.
I found that I could squeeze a bit more power out of my hash hack by adding these options:
This will force Hashcat to use the buggy but better performance CUDA GPU interface (–force), optimize for 32 characters or less passwords (-O), and set the workload to “Insane” (-w 4), which should do your computer is effectively unusable during the hacking process. Finally, “–opencl-device-types 1,2” will force HashCat to use BOTH GPU and CPU to process the hack.
Create a .hash file with all the hashes you want to crack puthasheshere.hash: $1$O3JMY.Tw$AdLnLjQ/5jXF9.MTp3gHv/
Hashcat example of cracking Linux md5crypt passwords using rockyou:
Hashcat example of WordPress password cracking using rockyou:
Sample hashes: http://openwall.info/wiki/john/sample-hashes
Not So Secure created a special rule:
https://www.notsosecure.com/one-rule-to-rule-them-all/
The rule can be downloaded from their Github site:
https://github.com/NotSoSecure/password_cracking_rules
I usually drop OneRuleToRuleThemAll.rule into the rules subfolder and run it like this from my Windows window (based on the notsosecure article):
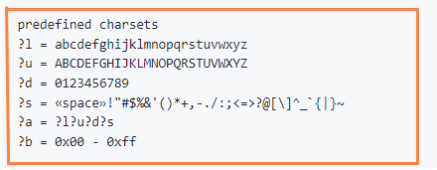
Selection of all passwords of length 1-8 with possible characters A-Z a-z 0-9
After grabbing or resetting the NTDS.dit and SYSTEM registry or resetting the LSASS memory from a Windows window, you often get NTLM hashes.
And using Impacket to reset the hashes
You can crack an NTLM hash dump by signing the following hashcat syntax:
A service principal name (SPN) is a unique identifier for a service instance. SPNs are used by Kerberos authentication to associate a service instance with a service login account. This allows the client application to request that the service authenticate the account even if the client does not have an account name. KRB5TGS – Kerberoasting accounts that use SPNs. After identifying the Kerberoastable service account (Bloodhound? Powershell Empire? – probably an MS SQL Server service account), any AD user can query it for the krb5tgs hash, which can be used to crack the password . Based on my benchmarking, KRB5TGS hack is 28 times slower than NTLM. Hashcat supports several versions of the KRB5TGS hash, which can be easily identified by the number between the dollar signs in the hash itself.
13100 – Type 23 – krb5tgs
19600 – Type 17 – krb5tgs
19700 – Type 18 – krb5tgs
18200 – ASREP Type 23 – krb5asrep
KRB5TGS Тип 23 – crackstation people only word list with OneRuleToRuleThemAll mutation rule list.
You may be prompted to recover your SMB (NTLMv2) authentication password from the packet capture. Below is a 9-step process to properly format your hash.
To crack Linux hashes, you must first remove their shadow
Hashcat seems to have issues with some zip hash formats generated with zip2john.
You can fix this by editing the contents of the zip hash to match the zip hash format example found on the hash cat example page:
PRINCE (PRObability INfinite Chained Elements) is a hashcat utility for randomly generating probable passwords:
Link: https://en.kali.tools/?p=1245
The Purple Rain attack uses a combination of Prince, a dictionary, and random Mutation rules to dynamically generate infinite password combinations.

