
A software product of the American company Acunetix, created for testing web applications for the detection of vulnerabilities, which has been in existence for more than 13 years and is used by both large companies in various fields of activity and personal affairs. Best suited for teams looking to secure their websites, web applications, and APIs. Acunetix automates routine testing for a cyber security professional and finds all common vulnerabilities, misconfigurations, weak points and filters threat types by category from minor to critical. Acunetix uses a multi-threaded scanner that provides the ability to scan hundreds of thousands of pages without interruption. Premium WordPress Vulnerability Detection – Scans your WordPress download and installation for over 1,200 known vulnerabilities in WordPress core, themes, and plugins. An easy-to-use login sequence logger that provides the ability to automatically scan complex password-protected areas.
Ability to review vulnerability data with built-in vulnerability management tools and quickly generate a variety of technical and compliance reports. It works on Windows, Linux and macOS. The product can be integrated with a number of issue tracking systems such as Atlassian JIRA, GitHub, GitLab, Azure DevOps, Bugzilla, Mantis. Can also be integrated with the Jenkins CI/CD tool. Macro recording technology scans password-protected pages and multi-level site forms. It has the highest level of vulnerability detection with a low rate of false positives compared to other competitors. Provides a detailed report that includes identified vulnerabilities as well as remediation suggestions. First of all, in the Acunetix report, you can view the structure of the site and all the pages of the site that the crawler has scanned. Acunetix also scans single page applications, web applications and complex web applications. It shows a list of vulnerabilities as well as the type of vulnerability in the report. Provides suggestions for eliminating identified vulnerabilities. Supports relevant compliance standards including HIPAA, ISO, NIST, OWASP Top 10, PCI DSS. Supports integration with web application firewalls such as F5, Fortinet, Imperva, Citrix, AWS. Since checking a large amount of code manually to detect all possible vulnerabilities is a complex task that requires a lot of time and a lot of expertise in different fields, we recommend using Acunetix and provide a step-by-step guide.

In this case, a local web application from DVWA (Damn Vulnerable Web Application) was used to investigate Acunetix PP.
Main page of PP Acunetix:
After saving the target, Acunetix prompts you to configure future scans.
The main thing to pay attention to is what type of scanning (Default Scan Profile) your TK needs from the customer
To begin with, these settings are sufficient to scan our web application.
Next, they offer to confirm the basic settings for the scanner.
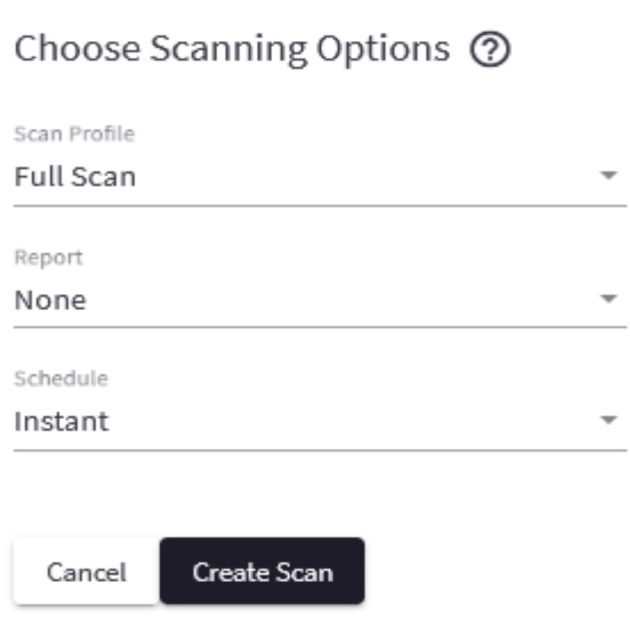
If you need to check the internal functionality of the site, you need to select the type of authorization and enter the appropriate data in the form.
Given the result of the scan, you can gradually analyze the received data.
Acunetix reports that it has found critical vulnerabilities that could lead to exploitation by cybercriminals. For example, records of site users from the database or use a backdoor in the code for their own purposes.
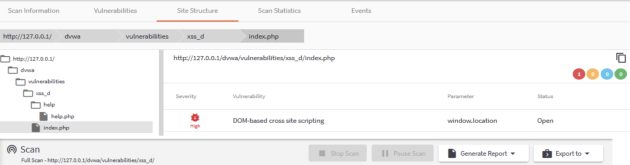
Vulnerabilities can be spotted immediately. The first priority was to find vulnerabilities at the address http://127.0.0.1/dvwa/vulnerabilities/xss_d/, the scanner detected the expected vulnerability reports on this web application page. The scanner also received reports of messages from the site’s web server, which also represents a potential threat. By clicking on a vulnerability, Acunetix provides a detailed report of the issue. Starting with the description of the attack that was successfully used by the Acunetix scanner, we observe the code that was used to find the security holes. A theoretical description of the threat in this case (XSS) was also written.
How this threat can be used by a web fraudster and how to fix this vulnerability.
Threat classification.
The following vulnerability was detected by the scanner as informative, that is, it does not represent a critical threat, but only reports information that a cybercriminal can obtain.
In this case, the criminal can obtain data about the language version used by the web server.
The following vulnerability was marked by the scanner as moderate. The scanner reports that fraudsters can obtain information about your Apache configuration and advises you to disable this permission if necessary.
Threat classification.
Here, out of interest, the scanner shows the tree of the scanning site and the final result with the vulnerability found.
This report is well structured and has data with critical vulnerabilities found by Acunetix PE.
We continue our research. As an example, we will look for a vulnerability in the form of authorization. Scan result.
Note that before setting the scan settings, the login and password data were not entered, this indicates that Acunetix has its own dictionary with frequently used weak passwords.
Vulnerability mitigation recommendations, classification, and attempts by an attacker to exploit this problem.
The next critical threat found by the scanner is open access to the website’s config file configuration.
The description of the vulnerability informs about the reason for finding this config file. The main thesis is that developers or site administrators create, consciously or unconsciously, with the help of code editors a backup of the main website config file.
The benefit to an attacker from this vulnerability is to inform the entire main knowledge base and relevant data of the website, which in turn provides the server address, name and passwords from the database, ports.
To check the vulnerability, it is enough to follow the link of the found backup file and open devtools in the browser, then go to the Network section and see the ready response that the server sent us to our request. It should also be noted that there is an Advanced section in the scan settings. The cookies section provides an opportunity to scan with existing data using (cookies). For example, the site has user and admin roles, the user (user) cookie will scan and look for vulnerabilities on the website to different sections of the site where open access is possible, but only for admins or for developers.
The technology section reports scanning to a separate MP of the website.
The header section will scan and check for vulnerabilities with the specified header data.

