
SSH is a set of programs that allow you to log into a remote machine to execute commands on it. It is designed to provide secure encrypted communication between two nodes over an unsecured network. X11 connections, arbitrary TCP ports, and UNIX domain sockets can also be forwarded over a secure channel. SSH includes programs that additionally allow you to transfer files over an encrypted connection. SSH includes various security enhancements, including user/host authentication, data encryption, and data integrity, which prevent popular attacks such as sniffing, DNS/IP spoofing, data forgery, connection interception ( connection hijacking), etc. Users of ftp, telnet or rlogin who use a protocol that transmits data in the form of clear text are advised to switch to SSH. SSH support is implemented in all UNIX systems, and most of them include an ssh client and server as standard utilities. You may need an SSH client to work with site files, to view and edit them, and to work with databases.
There are a number of SSH client implementations for non-UNIX OS as well. The protocol gained great popularity after the widespread development of sniffers, as an alternative solution to dangerous telnet for managing important nodes. The SSH protocol is developed on a commercial basis, and there is also a free version, OpenSSH, which is especially popular among web developers. OpenSSH is an open source implementation of the SSH protocol that allows you to encrypt network connections using a set of programs. If you want to have SSH on Linux, you can install OpenSSH, which consists of the OpenSSH server and client packages. The technology works according to the server-client principle. That is, on the remote machine on which you want to run the commands, you need to run an OpenSSH server. You can connect to this server using OpenSSH clients. Both the server and the client can be installed on one computer. Their launch and configuration are performed independently of each other.
So, on the server, sshd requires the main attention, and the sftp-server program will be launched automatically if necessary.
These are the basic programs that most users will need to generate keys, connect to a remote machine, and copy files.
For some configurations, the OpenSSH service is installed and enabled by default. This generally applies to systems that are difficult to access by any means other than SSH. For example, on VPS hosting (virtual private servers), the installed systems almost always have the SSH service installed and running, even in the minimal configuration, so after deploying a new server, the client just needs to connect using the credentials sent. In images for ARM computers, which often do not have a display, the OpenSSH service is usually already installed and running.
In Debain and derivatives (Kali Linux, Linux Mint, Ubuntu), OpenSSH programs can be installed separately, for example, there are packages for the client and for the server openssh-client and openssh-server.
Or you can install the ssh metapackage, which contains the client and server parts:
To install OpenSSH on Arch Linux, do:
On other Linux distributions, look for the openssh or ssh package.
The ssh client is launched by the user as needed. The OpenSSH service only needs to be running on the server.
So, if you want to use the first model (the SSH daemon is always active), type the following commands to start the service and add it to startup: They will add the SSH daemon to startup and start it right now.
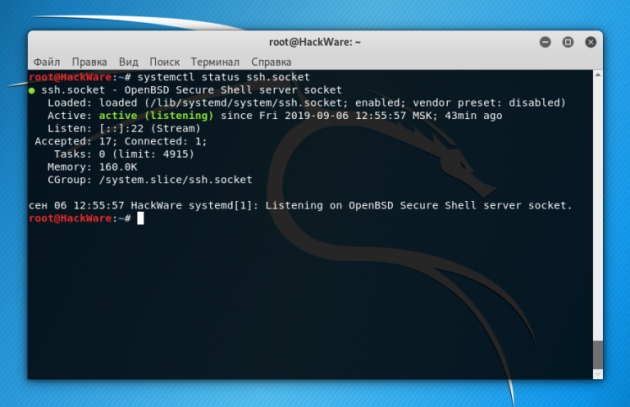
Note that in different distributions the service may be called ssh or sshd, so in the commands above and below, use the names:
sshd.socket
sshd.service
ssh.socket
ssh.service
start and stop this service
events related to user connections
You can view SSH logs in different ways, one of the options (remember that in some systems the service is called ssh.service, without the letter d):
For example, to display the last 100 records:
You can also view SSH events using:
Universal command regardless of service name:
If login using a public key is configured, but the password login option is not disabled, then after an incorrect key, you will be able to login with a password.
In case of an unsuccessful login attempt due to an incorrect key, at the default verbosity level (LogLevel) (INFO), special messages are not logged. Such unsuccessful attempts can be found under the record “Connection closed by authenticating user”, but this means disconnection at the authentication stage, regardless of the method of authentication – password or key. If you set the verbosity level to VERBOSE, then you can find in the log records of failed login attempts using the public key with the following command:



