

Every day we face new challenges in the field of cyber security, and DDoS (Distributed Denial of Service) attacks are becoming more sophisticated and destructive. In this article, we will look at effective strategies to protect against such attacks and the importance of testing systems to prevent them. In this article, you will find important information about strategies to protect against DDoS attacks and the importance of effective testing to prevent such attacks. We look at the different approaches and technologies that can be used to protect your digital assets, and emphasize the importance of continuous improvement in security systems. This article will provide you with knowledge of key strategies and solutions that will help you ensure your online presence is well protected against high-tech cyber threats. First of all, it is important to understand that a DDoS attack is an attempt to make an online service unavailable by overloading it with traffic from various sources.
Such attacks can cause serious disruptions to websites, servers and other online resources. One of the most effective defense strategies is the use of specialized DDoS protection systems that can detect and block suspicious traffic. It is also important to have a distributed content delivery network (CDN) that can distribute the load and reduce the risk of a single point attack. In addition to hardware solutions, attention should also be paid to information security. Regular software updates, using strong passwords, and two-factor authentication are basic steps to help protect your systems. Regular testing of your defense systems is important. Conducting penetration tests helps to identify potential weak points in the defense and eliminate them in time. Specialized firms can conduct such testing by simulating different types of attacks to check the readiness of the system to repel real threats.
Today I will tell you how you can test your IT infrastructure or application for resistance to DDoS attacks at the L4 and L7 levels. I will say right away that this cannot be called a serious load test, it is a simple and free test method.
He has two tasks:
Find out what the minimum capacity is enough for the infrastructure to start experiencing problems or go down completely. This is what we tested.
This technique can be used to evaluate the response speed of the used DDoS protection service. This is not about trying to satisfy the powerful filtering nodes of anti-ddos services from a single virtual machine. Rather, such a test will show how quickly the protection kicks in and begins to block malicious traffic, does it happen equally quickly for all types of attacks, and does it happen at all?
We will use MHDDoS for testing. This tool became famous during numerous DDoS attacks in 2022. The initial version of the program has been modified. It was modified for a large distributed infrastructure and made it possible to be added as a participant in DDoS attacks in a user-friendly way. Made a kind of DDoS as a service.
The choice fell on MHDDoS also because it is easily deployed on any infrastructure (written in Python) and has good documentation for an open-source project.
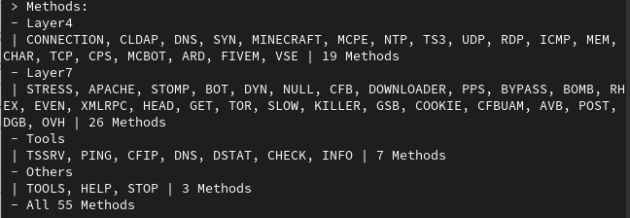
MHDDoS can attack at different levels – L4, L7. There are standard (syn-flood, tcp-flood), application-level attacks (post-, get-requests, s low Ddos), amplification attacks, and attacks tailored to specific services (Apache, for example). A total of 56 types of attacks for every taste.
The possibility of organizing an attack through a proxy and using different IP addresses is also claimed: the authors use 96 sources with open proxies, the lists of which are constantly updated. Using a proxy allows you to increase its power and make it more difficult to block. But we didn’t do that.
In addition, MHDDoS can be used to launch attacks aimed at bypassing DDoS services.
The program is a Python script. For container lovers, there is a Docker image. We download the script from Github, install the environment – and the software is ready for use.
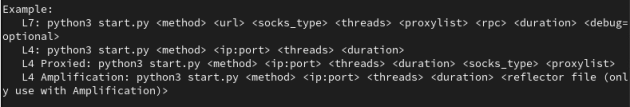
After starting, select the desired type of attack, for example, L7 get-requests. You specify which address to attack. In the case of an L7 attack, you can choose a specific URL where requests will go. You choose the power, the number of threads: how many requests will be generated per second.
Set the duration of the attack.
Also, for L7, the program requires you to select a proxy type and a list file. If we specify an empty file, the attack will go without a proxy. If there is no proxy, the program will offer to download a proxy from open sources.
As a stand, we will take two virtual machines (4 cores and 8 GB of RAM) with Rocky Linux, between which a 10G network is stretched. OWASP Juice shop will be deployed on the machine that comes under attack. It is usually used to study web vulnerabilities, but today it will be hit by a DDoS attack :).
No firewall rules, hit-count blocking rules, or other protection mechanisms are configured on the machine being attacked. In our case, the service will work over HTTP, and our machine will not have to spend additional resources on processing a TLS connection.
Under the hood, OWASP Juice Shop is a lightweight web service with a Node JS backend.
MHDDoS will accordingly be launched on the attacking machine.
L4. Let’s start testing with an attempt to clog the lane with generated packets. We choose a UDP attack. Let’s start with 100 threads:
sudo python3 start.py UDP owasp.nubes.ru:80 100 60 yes
At the peak, we get up to 80 Mbit/s, not much for UDP traffic. At this point, I tried running the program in single-threaded mode:
sudo python3 start.py UDP owasp.nubes.ru:80 1 60 yes
About 200 Mbit/c in UDP mode was obtained from one core, utilized at 100%, which is already much more serious. A 100-megabit channel can be jammed. The load on the RAM and CPU of the machine under attack practically did not increase.


As the second scenario, we will conduct an L4 TCP attack. Let’s attack the open SSH service:
sudo python3 start.py TCP owasp.nubes.ru:22 100 60 yes
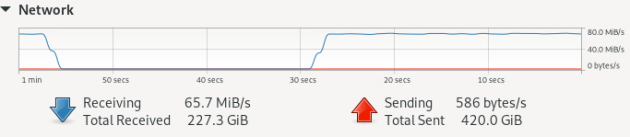
During the attack, it was possible to dispose of 100% of the RAM and CPU of the machine under attack. About half of the processors of the attacking machine were disposed of. With a DDoS attack from one IP address, the number of TCP connections increased slightly, with a full-fledged DDoS, this value can increase many times over.

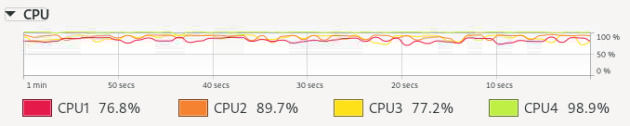
It turned out that the ratio of resources spent on the attack and utilized on the attacked server is approximately 1:2.
What conclusions can be drawn:
The minimum power required to bring down the server. If the service is not protected in any way, even such a “school” attack may be enough to download its infrastructure.
The minimum required power to clog the channel. In my case, I scored a 100Mbit bandwidth from one machine.
L7. For the L7 attack, I decided to try the proxies proposed by the authors. When the script is run for the first time with an empty proxy server, it polls lists of free proxies provided by developers. Although the script warns that the proxy check may take a long time, in my case, the process did not move for 4 hours, and patience ran out. Therefore, I did not succeed in attacking with the default proxy list.
Judging by the Telegram chat of the developers, I am not the only one who faced such a problem. Neither in the chat, nor on GitHub, I did not find any answers to this task. In general, the chat of this community is quite interesting for research. In addition to the discussion of MHDDoS, there are many offers for the sale of private proxies and more advanced DDoS scripts.
Later I made myself a free proxy list of 200 hosts with them and continued the attack. We run GET requests on OWASP Juice Shop. Here we must select the type of proxy, the file with the list of proxy servers and the number of connections to the servers.
sudo python3 start.py get http://owasp.nubes.ru/:80 0 100 proxy.txt 50 600 yes
What we have: the CPU on the machine under attack is completely disposed of, as well as 8 GB of RAM memory.
The load on the CPU of the attacking machine almost did not increase.

At the stage of planning the lab bench, I thought about how to measure the impact of a DDoS attack on the service and how to measure the slowdown in work.
But it did not help: in any mode, regardless of the number of threads, OWASP Juice Shop crashed a couple of seconds after launching the attack, issuing ERR_CONNECTION_TIMED_OUT in the browser tab. Services deployed in a container and using the classic method produced the same results.
Other things being equal, the resources spent on a DDoS attack are far less than those that will be utilized on the attacked server.
MHDDoS can be used to simulate DDoS attacks. It is possible to implement DDoS, but you will have to get proxy servers (in DDoS communities, private proxies for attacks are sold at a price of $20).
A small virtual machine or a home PC in the hands of a script kiddiz is enough to put a small web service or clog up a 100 Mbit Internet bandwidth.
Do not neglect DDoS protection, if even such free scripts can affect your infrastructure. As a basic measure, at least enable DDoS protection modules on network equipment. If there are none, make rules to block the number of connections from one IP. This will help in case of an attack from a small number of addresses. And if DDoS attacks are not uncommon for you, it is better to connect a specialized anti-DDoS service.

