

A VPN connection protects your internet connection. It routes all your network traffic through an encrypted tunnel through the VPN. Network traffic routing hides your IP address when you use the Internet by replacing it with the location and IP address from the VPN server, making its location invisible. A VPN connection also protects against external intrusions. There are many services, both free and paid. You just need to decide which one is right for you. One of such services is presented in this article. This is OpenVPN.
OpenVPN is a virtual private network (VPN) system that implements secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It implements both client and server applications. OpenVPN allows nodes to authenticate each other using pre-provided private keys, certificates, or username/password. When used in a multi-client-server configuration, this allows the server to issue an authentication certificate for each client using signatures and a certificate authority. OpenVPN is generally the most secure protocol you can find and is highly recommended by our experts. Protocol security checks revealed only minor issues that OpenVPN quickly resolved. When you use a secure VPN, you can extend that private network by making it virtual. Remote workers will be able to securely connect to your network using VPN connections while maintaining privacy online. In this article, we will talk about all the features of connecting to OpenVPN through a proxy or Tor.
1. Use TCP protocol. If you plan to connect to OpenVPN via HTTP/HTTPS proxy, to use TCP protocol instead of UDP, otherwise you will encounter an error:
Options error: –http-proxy MUST be used in TCP Client mode (i.e. –proto tcp-client)
But if you add the “–proto tcp-client” option to the command to connect to an OpenVPN server running on UDP, you will successfully connect to the proxy server, but the attempt to connect to OpenVPN will fail. Due to errors, the client will constantly try to reconnect to OpenVPN/
2. The use of a proxy will affect the performance of the network. The use of a proxy reduces the speed of transmission of traffic in the OpenVPN network, and also increases ping.
3. Configuring Squid Configuring the Squid proxy server to work with OpenVPN does not require any special options. For example, to use Squid as a proxy server to connect to OpenVPN without authentication, it is enough to specify the following lines in the configuration file (replace port 44220 with any other):
http_port 44220 acl portA localport 44220 http_access allow portA
Additionally, you can configure Basic or Digest authentication – OpenVPN supports them both
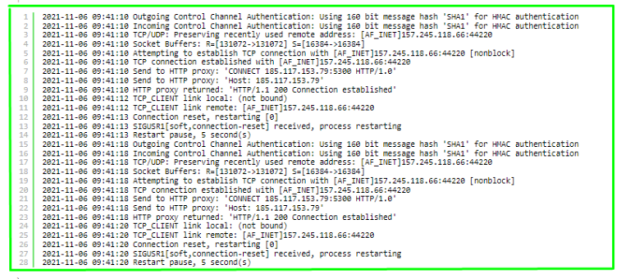
1. Client and server logs
The client and server logs should contain numerous references to the IP and port of the proxy server. For example, the output is:
Sample client log: as you can see, the connection is made from the proxy 157.245.118.66:44220; commands containing a link to the VPN server 185.117.153.79:5300 are sent to the proxy server:
2021-11-06 11:07:25 TCP/UDP: Preserving recently used remote address: [AF_INET]157.245.118.66:44220
2021-11-06 11:07:25 Socket Buffers: R=[131072->131072] S=[16384->16384]
2021-11-06 11:07:25 Attempting to establish TCP connection with [AF_INET]157.245.118.66:44220 [nonblock]
2021-11-06 11:07:26 TCP connection established with [AF_INET]157.245.118.66:44220
2021-11-06 11:07:26 Send to HTTP proxy: ‘CONNECT 185.117.153.79:5300 HTTP/1.0’
2021-11-06 11:07:26 Send to HTTP proxy: ‘Host: 185.117.153.79’
2021-11-06 11:07:27 HTTP proxy returned: ‘HTTP/1.1 200 Connection established’
2021-11-06 11:07:29 TCP_CLIENT link local: (not bound)
2021-11-06 11:07:29 TCP_CLIENT link remote: [AF_INET]157.245.118.66:44220
2021-11-06 11:07:29 TLS: Initial packet from [AF_INET]157.245.118.66:44220, sid=ae11f46a 0d3d585c
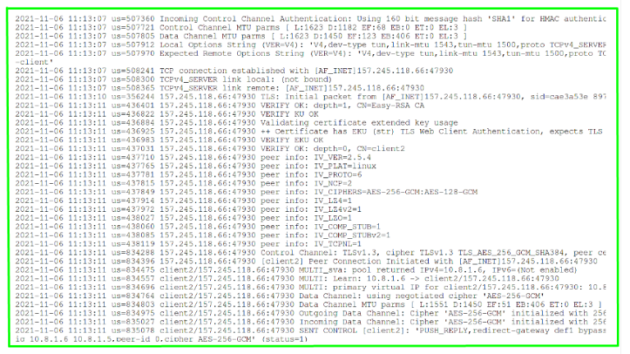
The openVPN server log says that the connection was made from a proxy IP address:
2021-11-06 11:13:07 us=508241 TCP connection established with [AF_INET]157.245.118.66:47930
2. Route of movement
When using OpenVPN connections, all routes are redirected via the IP address of the OpenVPN server. If the connection is made through a proxy, then in the user route settings, all connections are sent through the IP address of the proxy server.
The command for outputting routes:
ip route
Example of routes with OpenVPN connection disabled:
default via 192.168.1.1 dev lo1 proto dcp metrics 600 192.168.1.0/24 dev lo1 proto kernel scope link src 192.168.1.chh metrics 600
Let’s look at the routes on a client machine connected to the OpenVPN server:
ip route
As you can see, the routes mention the IP address 157.245.118.66, which is the address of the proxy server, not the OpenVPN server:
0.0.0.0/1 via 10.8.1.17 dev tun0 default via 192.168.1.1 dev wlo1 proto dhcp metric 600 10.8.1.1 via 10.8.1.17 dev tun0 10.8.1.17 dev tun0 proto kernel scope link src 10.8.1.18 128.0.0.0/1 via 10.8.1.17 dev tun0 157.245.118.66 via 192.168.1.1 dev wlo1 192.168.1.0/24 dev wlo1 proto kernel scope link src 192.168.1.44 metric 600
To connect to a remote host via HTTP, you must use the –http-proxy option and specify at least two arguments: the server address and the port number. For example, the command to connect directly to the OpenVPN server looks like this:
sudo openvpn client2.ovpn
It omits the –config option, which points to a configuration file. However, if you use other options, you must specify –config because the program will not be able to interpret the arguments correctly. Thus, the following command is identical to the previous one:
sudo openvpn –config client2.ovpn
To connect to OpenVPN through a proxy server, use a command like:
sudo openvpn –config client2.ovpn –http-proxy IP PROXY PORT PROXY
An example of a command to connect to OpenVPN through a proxy (proxy address 157.245.118.66 and port number 44220) without verifying the username and password:
sudo openvpn –config client2.ovpn –http-proxy 157.245.118.66 44220
You can specify the value of the –http-proxy option in the .ovpn configuration file, for example, if you specify the following line in the client2.ovpn file:
http-proxy IP PROXY PORT PROXY
Example:
http-proxy 157.245.118.66 44220
Then you can use the following command to connect to OpenVPN through a proxy – you don’t need to specify the proxy parameters in the command line:
sudo openvpn client2.ovpn
Basic authentication (in addition to the IP address and port of the proxy is required in any case) requires a login and password to access the proxy server.
The proxy username and password cannot be specified on the command line. This data must either be placed in a file with two lines:
КОРИСТУВАЧПАРОЛЬFor example, the login and password are placed in FILE-AUTHENTICATION.txt, then as the third argument of the –http-proxy option, you need to specify the path to this file and the command to connect through the proxy will be something like this:
sudo openvpn –config client2.ovpn –http-proxy IP-PROXY PORT-PROXY FILE-AUTHENTICATION.txt
Example:
sudo openvpn –config client2.ovpn –http-proxy 157.245.118.66 44220 authfile.txt
The username and password for proxy authentication can be placed in the .ovpn file using the following syntax:
USER PASSWORD
The above shows how to add the value of the –http-proxy option to the configuration file, so all the proxy connection settings can be collected in an .ovpn file as follows:
http-proxy IP PROXY PORT PROXY
USER
PASSWORD
If you did not specify FILE-AUTHENTICATION.txt or section <http-proxy-user-pass>…</http-proxy-user-pass>, then the proxy login and password will be asked of you in the console.
As the fourth argument of the –http-proxy option, you can specify an authentication method, it can be one of none, basic, or ntlm. For NTLM authentication, specify ntlm, for example:
sudo openvpn –config client2.ovpn –http-proxy 157.245.118.66 44220 authfile.txt ntlm
You may have noticed that there is no option for HTTP Digest authentication, but this type of authentication is supported. It is enabled using the auto or auto-nct flags, which must override the FILE-AUTHENTICATION argument. That is, it turns out that the login and password will need to be specified in the .ovpn file or entered manually in the console. Configuring a proxy connection with Digest authentication in the .ovpn file:
http-proxy IP-PROXY PORT-PROXY auto
USER
PASSWORD
The auto flag causes OpenVPN to automatically determine the authentication method. The auto-nct flag (meaning “no clear-text auth”, i.e. no clear-text authentication) instructs OpenVPN to automatically determine the authentication method, but to reject weak authentication protocols such as HTTP Basic Authentication. Examples:
Since the Tor network uses the SOCKS protocol, you might think that connecting to OpenVPN through the Tor network is just a special case of connecting through a SOCKS proxy, but in practice you need to remember that the Tor network does not transmit UDP traffic. But this is only the beginning. You cannot use Tor as a proxy for OpenVPN if Tor is running on the same machine you are trying to connect to the VPN server with. To understand why such a connection is basically impossible, consider what happens when using a VPN. When we connect to a VPN (without a proxy or Tor), new routes are set up on the local computer:
If you connect to a VPN through a proxy (for example, through Tor), the following routes are added:
So, if the proxy server is on another computer, it works without problems. But if the LOOPBACK (localhost) IP address of the proxy server is specified, the following set of rules is obtained:
That is, the system closes itself. Yes, it is possible to connect to a VPN through Tor even if the Tor service is running on the same computer. But immediately after that, the VPN adds the routes necessary for operation, which tightly block the movement of traffic – it can leave the computer. This problem can be solved if you connect through Tor running on another computer, even on the same local network, even using virtual machines. An example of a working configuration with a virtual machine: a real computer acts as a proxy with Tor running, and the connection to OpenVPN through the Tor proxy is performed from a virtual machine. The reverse option – connecting to OpenVPN from a real machine through a virtual proxy machine will not work. You can use two virtual machines, one of which will be a proxy with Tor running, and the other will be used to connect to OpenVPN. It is for this reason that the Whonix distribution has two halves – the main OS and the gateway.
You can use Tor as a VPN proxy as:
On the computer acting as a proxy through Tor, install the tor package.
On Debian, Kali Linux, Linux Mint, Ubuntu, this is done with the command:
sudo apt install tor
In Arch Linux, BlackArch, Manjaro, installation is performed by command
sudo pacman -S tor
By default, the tor service allows incoming connections only from localhost, that is, connections from other computers are not accepted.
Open the file /etc/tor/torrc
sudo gedit /etc/tor/torrc
and add a line of the type to it:
SOCKSPort EXTERNAL_IP:9050
Example:
SOCKSPort 192.168.1.39:9050
Start tor services:
sudo systemctl start tor
You can add tor to autoboot:
sudo systemctl enable tor
You can now connect to the OpenVPN server via Tor running on the remote computer:
sudo openvpn –config client5.ovpn –socks-proxy 192.168.1.39 9050
Privoxy can be used as an HTTP proxy → SOCKS proxy adapter. That is, the OpenVPN client will connect to Privoxy as an HTTP proxy, and Privoxy will redirect traffic to Tor, which uses the SOCKS protocol. Install the tor and privoxy packages on the Tor proxy computer.
On Debian, Kali Linux, Linux Mint, Ubuntu, this is done with the command:
sudo apt install tor privoxy
In Arch Linux, BlackArch, Manjaro, installation is performed by command
sudo pacman -S tor privoxy
To configure Privoxy on the computer that will act as a proxy through Tor, the file /etc/privoxy/config
sudo gedit /etc/privoxy/config
add the line:
forward-socks5t / 127.0.0.1:9050 .
By default, Privoxy only accepts incoming connections from the same computer, to make Privoxy start accepting connections from, replace the line
listen-address 127.0.0.1:8118
on
listen-address :8118
If you want connections to be accepted only from the local network, specify the local IP address
listen-address 192.168.1.20:8118
Start the tor and privoxy services:
sudo systemctl start tor privoxy
You can add these services to autoboot:
sudo systemctl enable tor privoxy
By default privoxy listens on port 8118, also specify the IP address of the computer running privoxy and Tor
sudo openvpn –config client5.ovpn –http-proxy 192.168.1.39 8118
Due to the specifics of the Tor network, the connection may not happen the first time, and the connection may be slow and unstable.