

Tor is short for “The Onion Router”, which refers to several layers of encryption used to protect your privacy. The main function of Tor is that it hides your tracks on the Internet, allowing you to browse and download web pages anonymously. But let’s be clear that Tor is not a VPN service or a browser with a built-in VPN. Although both Tor and VPN allow for private web browsing, they are very different technologies. The Tor network hides your identity by routing your internet activity through different Tor servers. This allows you to have complete anonymity and security from anyone trying to track your activity, such as governments, hackers and advertisers. Tor not only hides Internet activity, but also helps bypass censorship.
The Tor network is a path to the “dark side of the Internet” – a part of the digital world that guarantees anonymity, is not subject to censorship and lives by its own strict laws. However, such high security comes at a price: connecting to Tor takes a few seconds, and the data transfer speed is relatively slow. Fortunately, all the serious technology behind Tor does not make it difficult and inaccessible to the average user. Working with the Tor browser is not too different from interacting with a regular browser. Tor is portable software that doesn’t integrate with Windows, meaning you can run the browser from anywhere on your computer, even from a USB drive. Therefore, every average user can get started with the Tor browser. Therefore, this article will talk about the capabilities and limitations of the Tor network, as well as several programs that will increase your anonymity by hiding your real IP.
The Tor network is primarily designed to provide anonymity to users when accessing the Internet by hiding their real IP address. Data transmitted over the network is encrypted, but at the source node, which makes a direct request to the site and receives a response from it, the traffic is in its original state (that is, the traffic that is encrypted by third-party means, for example, HTTPS – it is encrypted, and traffic transmitted in plain text is available to the source node in unencrypted form).
The Tor network is also designed to access websites, for this reason, and to avoid collecting user fingerprints (such as operating system version by network packet specifics), the Tor network supports a very limited set of transmitted traffic. For example, it is possible to request a website through the Tor network (TCP protocol), but it is not possible to transmit UDP packets or raw packets (anything but a full connection to the site is prohibited). The Tor network is suitable for:
For this reason, when we say “redirect all traffic through Tor” we really mean “redirect all traffic supported by this network through Tor. Much of the traffic simply cannot be sent through the Tor network, such as pings, some tracing methods, half-open connections scanning, UDP DNS queries, et c. Based on this, another question arises – what to do with traffic that cannot be transmitted through the Tor network: send it to the target host by bypassing the Tor network or block it?
When configuring the system to use Tor, you can choose different implementation options: proxy or iptables. When setting up a proxy, you need to remember that Tor works as a SOCKS proxy — not all programs support this protocol. But the most annoying thing can be that if system-wide proxy settings are set, some programs can ignore these settings and connect to remote hosts directly, bypassing proxies and Tor. In this sense, the iptables program is a more reliable and versatile option, which, if properly configured, will ensure that one or another type of traffic cannot leave the system except through the Tor network, or will be blocked. So, as we have already learned, it is necessary to solve a number of tasks in order to work correctly with Tor:
For this reason, there are many different programs from different authors that implement the described functionality to one degree or another.
Although all the programs discussed below are slightly different, let’s start with the most unusual of them. It is called orjail. The program creates its own network environment for the running program at startup, and in this environment the program can access the Internet only through the Tor network.
Installation in Kali Linux

Installation in BlackArch
For the program to access the network through Tor, run a command like this:
sudo orjail PROGRAM ARGUMENTS
For example, the following command shows the external IP of your computer:
curl suip.biz/ip/
Now let’s run the same command using orjail:
sudo orjail curl suip.biz/ip/
Please note that the Tor service does not need to be running. The orjail program itself creates virtual network interfaces, starts a new instance of Tor itself, and when the main program terminates, stops Tor and removes the temporary network interfaces. To see this clearly, look at the information about your network interfaces:
ip a
Now look at what programs run with orjail see:
sudo orjail ip a
They are in a completely different environment!
In this way, you can also run programs with a graphical user interface:
sudo orjail firefox -P /tmp/tmpprofile
But be careful with web browsers: either it’s more of a super quick fix when you need to bypass blocking or change your IP. In more serious situations, use the Tor Browser – this option is safer.
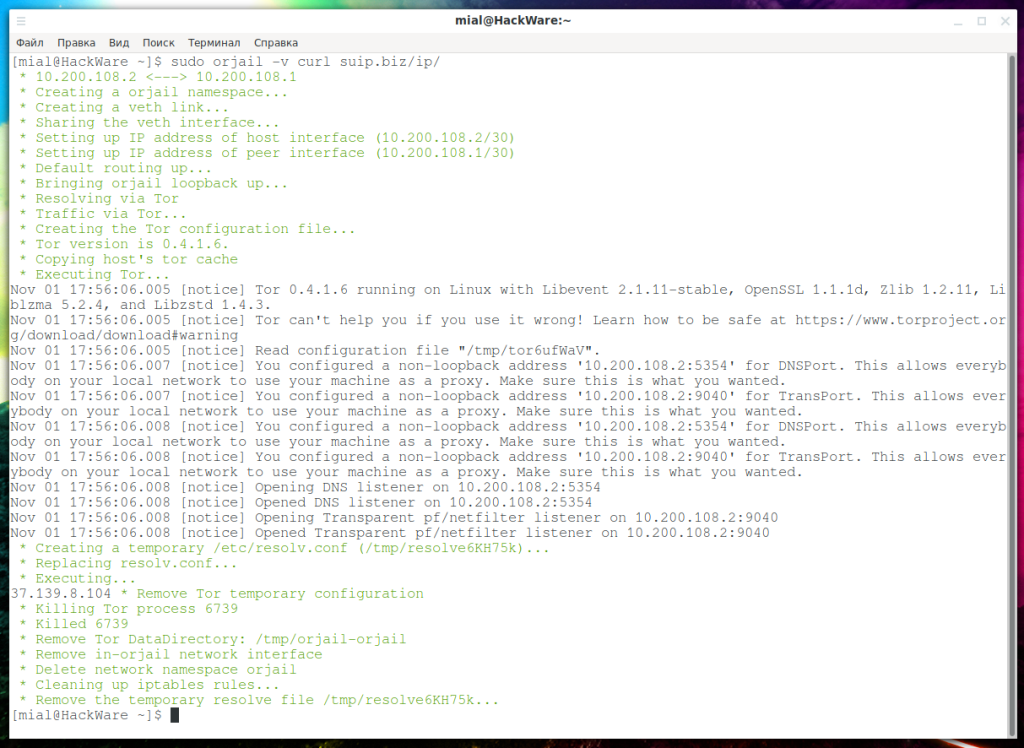
If you run orjail with the -v option, you can see all the processes taking place:
sudo orjail -v curl suip.biz/ip/
Please note that orjail does not support IPv6! The fact is that the created temporary network interfaces are assigned only IP addresses. In principle, I think it is easy to add IPv6 support, but now IPv6 traffic is simply not going anywhere.
 й
й
As we already know, it is not possible to send UDP packets through Tor, but orjail can perform DNS queries:
sudo orjail dig suip.biz
As the server from which the DNS response was received, something like:
10.200.194.2 # 53
That is, DNS requests are processed in the Tor network.
Error “User root: invalid name or no home directory.”
You may encounter an error:
User root: invalid name або no home directory.
where instead of root will be the name of your user.
This is what the error looks like when debugging information is displayed:
To fix, open the orjail file (if you have already done the installation, then this file is located in the /usr/sbin/orjail path), find the line
USERHOME = $ (getent passwd les | cut -d: -f 6)
And replace with:
USERHOME=$(getent passwd $USER | cut -d: -f 6)
Error “./usr/sbin/orjail: line 563: /tmp/torpVKzn4: Access is denied”
This is an example of an error. Instead of /tmp/torpVKzn4 can be any arbitrary name.
To fix it, open the orjail file again (if you have already installed, then this file is located in the /usr/sbin/orjail path), find the line
chown “$USERNAME” “$TORCONFIGFILE”
and replace with
#chown “$USERNAME” “$TORCONFIGFILE”
Further, such programs are very similar, they all use Tor + iptables, but everything is slightly different. Let’s start with the multipurpose program torctl. This program is written for BlackArch, but is easily ported to other distributions.
Installation in Kali Linux
Installation in BlackArch
sudo pacman -S torctl
torctl ip
To run Tor as a transparent proxy:
sudo torctl start
To check the status of services:
torctl status
If you want to change your IP on the Tor network:
sudo torctl chngid
To return the source MAC addresses:
sudo torctl rvmac
To change MAC addresses on all network interfaces, run the command:
sudo torctl chngmac
To work with the Internet directly without Tor, run:
sudo torctl stop
To disable this feature:
sudo systemctl disable torctl-autowipe.service
This command will add the torctl service to startup:
sudo systemctl enable torctl-autostart.service
You can enable automatic memory cleaning every time the computer is turned off:
sudo systemctl enable torctl-autowipe.service
To remove a service from startup, do the following:
sudo systemctl disable torctl-autostart.service
If you are familiar with Parrot Linux, then you should also be familiar with AnonSurf – it includes an incognito mode in the sys AnonSurf optionally closes applications that can compromise anonymity, redirects traffic and DNS requests through Tor, blocks IPv6. AnonSurf is too integrated in Parrot Linux and on other systems I would recommend choosing some other option, good thing there is a choice. I also don’t like the fact that the program tries to start/stop some services without checking their presence and displays errors if they are not there – because of the excess of unnecessary information, something really important can be missed. Nevertheless, the following shows how to install AnonSurf on Kali Linux. Most of the functionality is preserved, but the command “dns – Replace your DNS with an OpenNIC DNS server” will not work!
Installation in Kali Linux
Showing your external IP address:
sudo anonsurf myip
Start redirecting all traffic through the Tor network:
sudo anonsurf start
Termination of Tor traffic redirection:
sudo anonsurf stop
Nipe is a script that makes the Tor network your default gateway. This Perl script allows you to direct all your traffic from your computer to the Tor network, through which you can access the Internet anonymously without having to worry about your IP being tracked or IP-calculated. Nipe currently only supports IPv4, but work is underway to add IPv6 support.Tor Router allows you to use the Tor network as a transparent proxy and send all your traffic, including DNS requests, through Tor. The Tor network will become the default gateway for all Internet connections, increasing privacy/anonymity with minimal effort. The script will run on any system that uses systemd (if you want to use this tool as a service) and tor.
Tor Router allows you to use the Tor network as a transparent proxy and send all your traffic, including DNS requests, through Tor. The Tor network will become the default gateway for all Internet connections, increasing privacy/anonymity with minimal effort. The script will run on any system that uses systemd (if you want to use this tool as a service) and tor. Tor Router doesn’t modify system files like other tools do to route your traffic, so with minimal system impact, in the event of a TOR Router service failure or removal of this tool, the rest of your system will not be affected. Tor-router currently only supports IPv4 traffic, but the author plans to add IPv6 support.
The Tor Iptables script is an anonymizer that configures iptables and tor to redirect all services and traffic, including DNS, through the Tor network. I already talked about this script in more detail in the article “How to quickly change IP in Linux”. I wouldn’t recommend using the last three scripts until IPv6 is added to them, otherwise you can accidentally screw things up a lot.
Tor Browser is a fully customizable and portable browser for browsing websites through the Tor network. The advantages of this option are additional measures for anonymity. The cons follow from the pros: the more measures for anonymity, the more inconvenient to use.

